In this post, I’ll show you some applications of cryptography in network security.
Current cryptographic algorithms are hard to understand, some of them use complex mathematics as their basic building blocks. Sometimes, this fact makes it difficult for us to see how we can apply these algorithms to provide security in a network.
So, let’s start by defining what cryptography is.
“Cryptography encompasses the study of methods and techniques to secure information, so people without required permissions cannot have access to it.” Source.
Notice that what we want to achieve is to secure information. This is usually done through an information security system. This type of system usually involves certain components, such as:
- Internet
- Intrusion Detection System
- Demilitarized zone
- Firewall
- Local Area Net
- Firewall, backup, internal servers, etc.
Now, let me explain how some of the components are implemented by using cryptographic techniques.
Table of Contents
Applications of Cryptography in Authentication
We need to have user authentication mechanisms in place to determine who has access to the network. These mechanisms are used at different levels of services.
For instance, a firewall won’t allow a client to connect to a network or service if the user is not authenticated, or if the authenticated user does not have permission to access the specific service.
We can apply cryptography in different ways to provide user authentication mechanisms.
User authentication can be divided into two steps.
The first is to present credentials. This is when the user presents a card, ID document, user and password, etc.
The second step is verification. This step is when the credentials are verified, to determine if they are not fake and the level of access the user has.
Workstation Authentication
Probably the most used method is the user and password combination. This one is used mostly in operating systems to determine if you have access or not.
Operating systems, like Windows or Mac OS, do not store the passwords in plain text. The reason behind this is that anyone with access to the system (sometimes computers are shared in the workplace and at home) will have access to the password of other users, which is a big security flaw.
Instead, they usually create a cryptographic hash of the password. What the operating system store is the hash instead of the plain text.
When a user presents the credentials, the operating system creates the hash of the password the user entered and compares it with the hash stored in the system. If they match, the user gets access to the system.
Distributed environment authentication
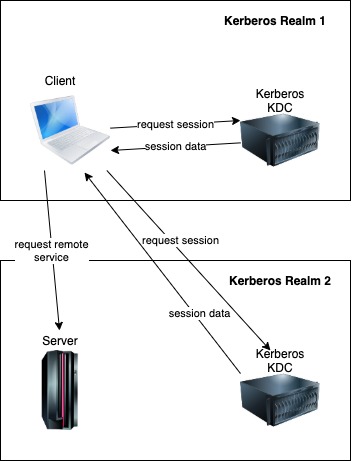
Another situation that is related to user authentication is when there are several computers in a distributed environment, there are also several services, and client computers need access to the services.
In this scenario, the servers distributed throughout the network cannot trust that the clients can properly identify the users. The reason behind it is because of the following threats:
- “A user may gain access to a particular workstation and pretend to be another user operating from that workstation.
- A user may alter the network address of a workstation so that the requests sent from the altered workstation appear to come from the impersonated workstation.
- A user may eavesdrop on exchanges and use a replay attack to gain entrance to a server or to disrupt operations.” Cryptography and Network Security by W. Stalling.
One of the solutions to this situation is Kerberos: the network authentication protocol. Computer scientists from MIT created Kerberos in the 1980s.
Kerberos uses symmetric cryptography and a Key Distribution Center (KDC) to authenticate users in a distributed network environment.
Personal identity verification
Another type of authentication is based on (smart) cards that a user can possess.
There is a standard for Personal Identity Verification of Federal Employees and Contractors created by NIST. The purpose of this document is to establish “a standard for a Personal Identity Verification (PIV) system that meets the control and security objectives of Homeland Security Presidential Directive-12. It is based on secure and reliable forms of identity credentials issued by the Federal Government to its employees and contractors.”
The standard has cryptographic specifications for:
- PIV authentication key. A mandatory asymmetric private key that supports card and cardholder authentication for an interoperable environment.
- Asymmetric card authentication key. A mandatory private key that supports card authentication for an interoperable environment.
- Symmetric card authentication key (deprecated) An optional symmetric key that supports physical access.
- Digital signature key. An asymmetric private key that supports document signing.
- Key management key. An asymmetric private key that supports key establishment.
- PIV Card application administration key. An optional symmetric key used for personalization and post-issuance activities.
- PIV secure messaging key. An optional asymmetric private key that supports key establishment for secure messaging and card authentication for physical access.
The PIV Card store private keys and corresponding public key certificates and perform cryptographic operations using the asymmetric private keys.
Applications of Cryptography in Web Security
There are many cryptographic applications in web security. Here, I will just mention a few without going into much detail. But you can follow the links provided to go deeper into each topic.
SSL/TLS
Authenticated Encryption (AE) is an encryption approach that addresses confidentiality and authenticity at the same time. The approach is to generate two keys, calculate the message authentication code using the first key, and encrypt the message plus the message authentication code using the second key.
SSL/TLS protocol uses this approach.
Some of the algorithms defined in the specification for the SSH transport layer protocol are:
- 3des-cbc, REQUIRED, three-key 3DES in CBC mode
- blowfish-cbc, OPTIONAL, Blowfish in CBC mode
- twofish256-cbc, OPTIONAL, Twofish in CBC mode, with a 256-bit key
- twofish-cbc, OPTIONAL, alias for “twofish256-cbc”
- twofish192-cbc, OPTIONAL, Twofish with a 192-bit key
- twofish128-cbc, OPTIONAL, Twofish with a 128-bit key
- aes256-cbc, OPTIONAL, AES in CBC mode, with a 256-bit key
- aes192-cbc, OPTIONAL, AES with a 192-bit key
- aes128-cbc, RECOMMENDED, AES with a 128-bit key
HTTPS
“Hypertext Transfer Protocol Secure (HTTPS) is an extension of the Hypertext Transfer Protocol (HTTP). In HTTPS, the communication protocol is encrypted using Transport Layer Security (TLS) or, formerly, Secure Sockets Layer (SSL).” Source.
So, HTTPS also uses the cryptographic protocols embedded into SSL/TLS.
SSH
One of the protocols we can use to securely communicate in an unsecured network is Secure Shell (SSH).
SSH is the protocol that most people choose to use for remote login and tunneling.
This protocol uses asymmetric cryptography to encrypt the communication between the client and the server.
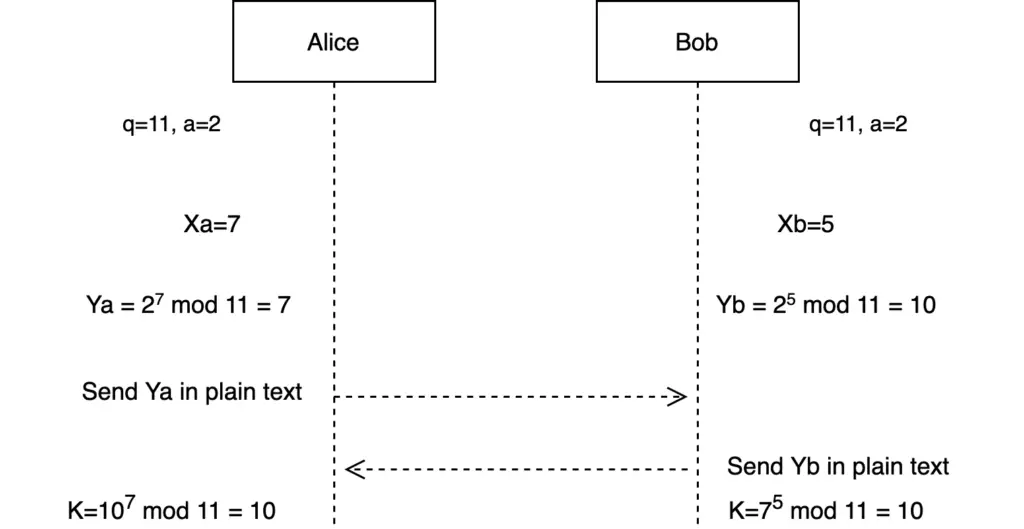
Specifically, it uses the Diffie-Hellman Key exchange to securely exchange the cryptographic keys.