Man-In-The-Middle (MITM) attack is one of many approaches that attackers or hackers use to steal or get unauthorized access to information.
The MITM attack is a well-known attack where an attacker intercepts the information transmitted in a communication. At that point, the attacker can just resend the same information or modify it and re-send it. This type of attack can be active or passive. It is a passive attack If the attacker just listens to the communication. However, if the attacker intercepts the communication and tampers it, then it is an active attack.
Let’s see how it works and one example.
Table of Contents
- General scheme of a Man-In-The-Middle Attack
- Example of a Man-In-The-Middle Attack to the Diffie-Hellman Key Exchange
- How to prevent the MITM attack
General scheme of a Man-In-The-Middle Attack
In the figure below you can see the general approach that an attacker follows to perform a MITM attack.
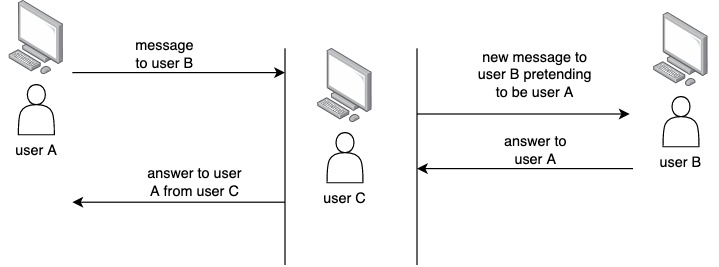
Here is how it works:
- User A sends a message to user B
- The attacker (user C) intercepts the communication, and send a new message to user B (the original recipient of user A message)
- User B sends back an answer to user A
- The attacker intercepts the answer from user B
- The attacker then sends another answer to user A
This attack is possible when the protocol used for sending the information does not authenticate the sender and the recipient.
Example of a Man-In-The-Middle Attack to the Diffie-Hellman Key Exchange
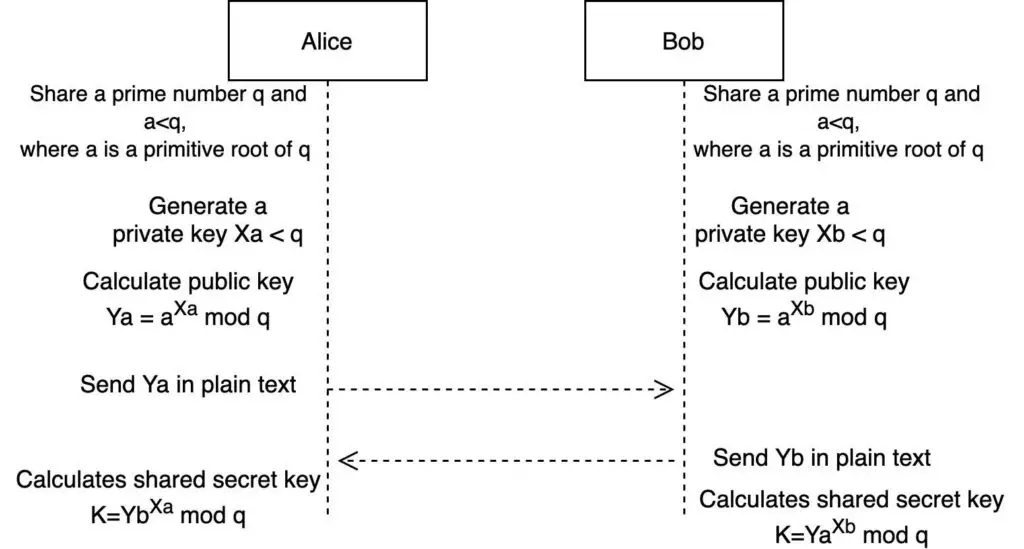
Let’s explore an example of what can happen if you use the Diffie-Hellman key exchange.
Find below the Diffie-Hellman key exchange scheme. If you are not familiar with this algorithm, you can read this post.
When Alice and Bob share the prime number q and a, the attacker that is listening to the communication, intercepts the values and creates two public keys Y1 and Y2, and the corresponding private keys X1 and X2.
When Alice sends her public key to Bob, the attacker intercepts the communication and replies to Alice with public key X1. At the same time, it sends the second public key Y2 to Bob.
Alice calculates her shared secrete key using the attacker public key Y1.
The attacker calculates the shared secret key (with Alice) using Alice’s public key.
Bob calculates his shared secrete key using the attacker public key Y2.
The attacker calculates the shared secret key (with Bob) using Alice’s public key.
From now on, the attacker can decrypt any communication between Alice and Bob and can send encrypted information to the two of them.
Let’s see this process in the picture below.
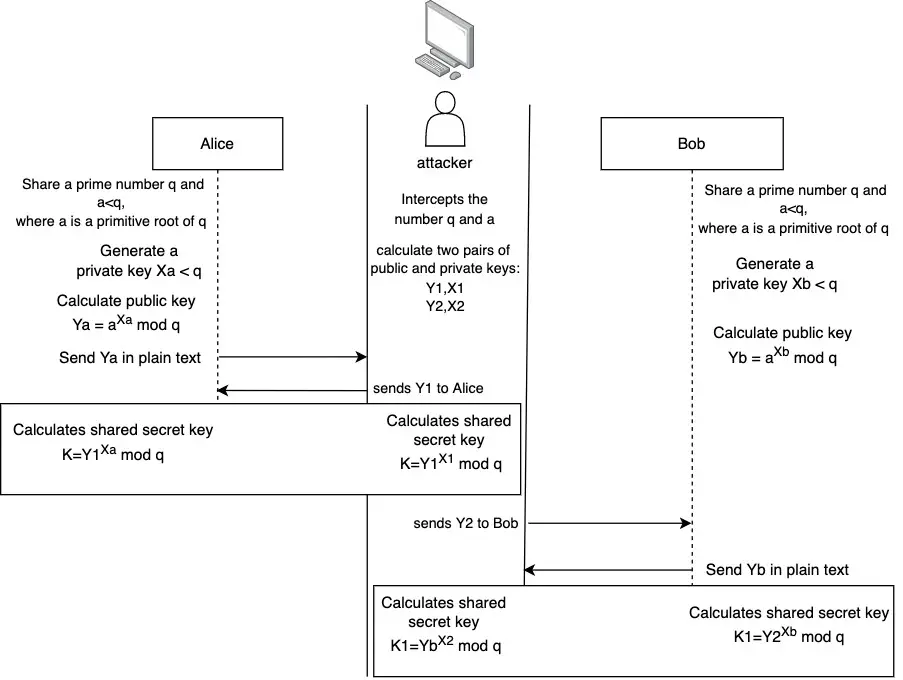
Notice that the secret key K is shared between Alice and the attacker and the secret key K1 is shared between Bob and the attacker.
After the three users calculate the shared secret keys, the MITM attack is complete.
How to prevent the MITM attack
The main reason this type of attack can succeed is when the protocol or scheme we use does not authenticate the participants in the communication.
From there, you can see that two of the ways we can easily avoid this type of attack is by using:
- Digital signatures. You can learn more about Digital Signatures in this post.
- Public Key Certificates, also known as digital certificates. You can find out what a digital certificate is here.
Related topics
What is a replay attack in Cryptography?
