What is a masquerade attack in network security?
A masquerade is an attack where the attacker pretends to be someone else to gain unauthorized access to information or services.
This attack is classified as an active attack. Also, it usually includes another type of active attack, like a man-in-the-middle attack, modification of messages, etc.
Understanding a masquerade attack
There are many examples of this type of attack in real life that you probably were the target.
One of the most common examples is when you receive an email like the following:
Congratulations from Company X !!
We choose your email as one of the lucky winners and you won $ 1 000 000.
…
Click the link below to claim your prize.
Once you click the link, they will ask you for your bank account details so they can transfer you the money.
Usually, “Company X” is a well-known company that you probably trust. So, the attacker pretends to be that company to get access to your bank account detail.
Another example is an attacker that intercepts a communication between two parties, then modifies the communication for personal gain. Let’s see an example of communication.
User A sends the following message to user B.
Pay $ 10 000 to Sam’s bank account.
The attacker intercepts the message coming from user A, and send the following new message to user B:
Pay $ 10 000 to Bob’s bank account. Where Bob’s bank account is the attacker’s bank account.
See below a graphical example of the previous attack.
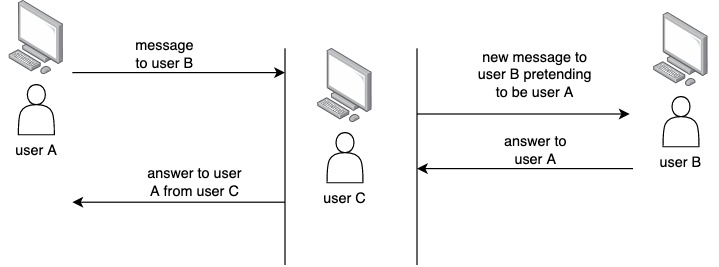
Notice that the attacker (user C) pretends to be user A when communicating to user B, and also pretends to be user B when communicating with user A.
Related topics
