The Open System Interconnection (OSI) security architecture is a recommendation of the International Telecommunication Union which defines a systematic approach to define security requirements for a certain organization, as well as approaches to meet the aforementioned requirements.
The OSI security architecture provides a general description of security services and mechanisms, as well as a description of security attacks.
Table of Contents
- Definitions
- Security Attacks
- Security Services
- Security Mechanisms
- Security services and mechanisms and the OSI Reference Model
Definitions
Security attack: Any action that compromises the security of information owned by an organization.
• Security mechanism: A process (or a device incorporating such a process) that is designed to detect, prevent, or recover from a security attack.
• Security service: A processing or communication service that enhances the security of the data processing systems and the information transfers of an organization. The services are intended to counter security attacks, and they make use of one or more security mechanisms to provide the service.
Threat: A potential for violation of security, which exists when there is a circumstance, capability, action, or event that could breach security and cause harm. That is, a threat is a possible danger that might exploit a vulnerability.
Attack: An assault on system security that derives from an intelligent threat; that is, an intelligent act that is a deliberate attempt (especially in the sense of a method or technique) to evade security services and violate the security policy of a system.
All the definitions are taken from the book Cryptography and Network Security by William Stallings.
Security Attacks
A security attack is an activity or act made upon a system with the goal to obtain unauthorized access to information or resources. It is usually carried out by evading security policies that are in place in organizations or individual devices.
Security attacks can be passive or active.
A passive security attack is one where the attacker just listens to or monitors a communication. In this case, the attacker will not impersonate any of the parts of the communication. See an example in the figure below.
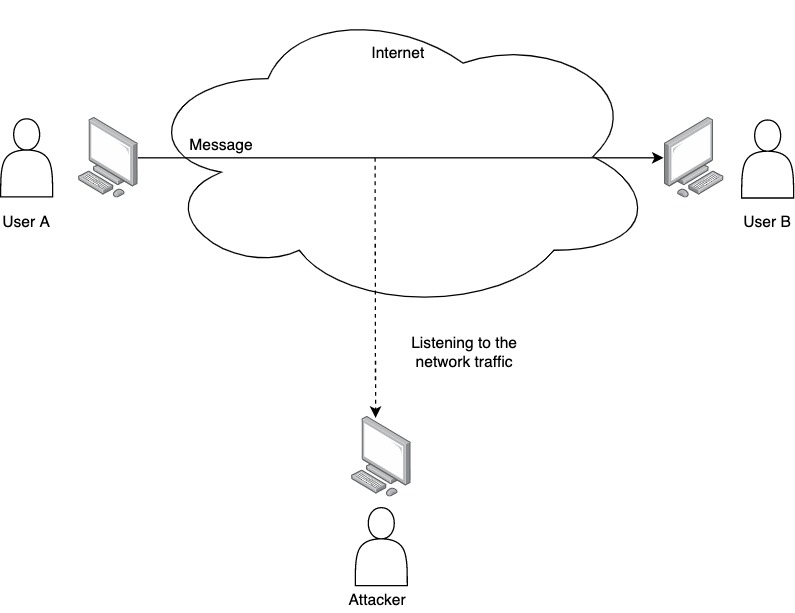
Some of the passive attacks are:
- Release of message contents. This happens when the attacker can intercept confidential information: bank statements/account documents, payslips, etc.
- Traffic analysis. In this case, the attacker just listens to the traffic to gain knowledge that is not public. As an example, an attacker is listening to a communication between a famous actress and her manager. The communication shows where the actress will spend her holidays. She probably doesn’t want that information to be in hands of the paparazzi. One way of doing traffic analysis is using a Man-In-The-Middle (MITM) attack. In this post, I explain this attack in more detail and show that it can be active or passive.
The way to prevent this type of attack is by using encryption. If the communication is encrypted using secure mechanisms, then it does not matter if an attacker listens to the communication, because the attacker won’t be able to make any sense of it. I wrote a post for you to understand the general concepts to study cryptography.
On the other hand, is an active attack, the attacker will modify the information that is transmitted and try to impersonate one or both parties in the communication. Another type of attack is when the attacker creates a message and starts a communication pretending to be someone else in order to gain access to sensitive information, get someone to do something, or cause a denial of service.
See a general representation below.
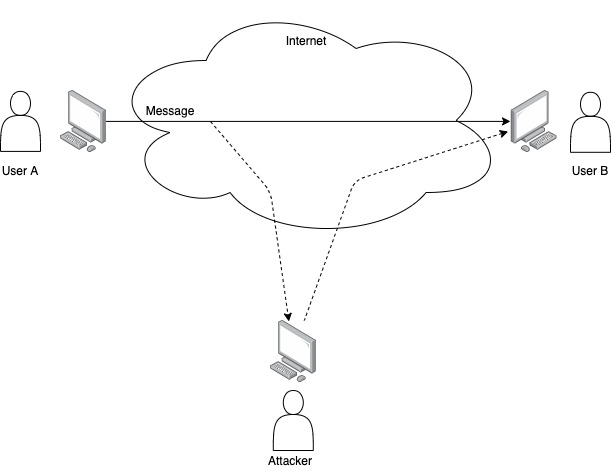
Some examples of active attacks are:
- Masquerade attack. When the attacker impersonates someone else. This type of attack is usually used together with another attack, like reply and modification attacks. You can find an article with an explanation and example here.
- Reply attack. In this type of attack the attacker capture the data that is transmitted and re-sends it to produce an unauthorized action. A post with a deeper explanation is in this link.
- Modification of messages. This type of attack happens when the attacker capture information, modifies it, and re-sends it to produce an unauthorized action. This type of attack can be carried on as a Man-In-The-Middle attack. You can learn more about MITM here.
- Denial of service. This type of attack occurs when a service is prevented to work as expected. Usually, it also brings as consequence, other services or users are also prevented to do their duties. As an example, imagine that an e-mail is sent to a person with instructions to perform a time-sensitive task. At the same time, a Denial of Service (DoS) attack is performed on the email server. As a consequence, the person cannot read the email (the server is down) and cannot carry on the instructions (the person’s duty).
I wrote a post that answers the question what is a security attack? so you can have more information.
Security Services
According to the Internet Security Glossary Version 2 (RFC 4949), a security service is “A processing or communication service that is provided by a system to give a specific kind of protection to system resources”.
The OSI security architecture classifies security services as follows:
- Authentication:
- Peer entity authentication
- Data origin authentication
- Access Control Service
- Data Confidentiality:
- Connection confidentiality
- Connectionless confidentiality
- Selective field confidentiality
- Traffic flow confidentiality
- Data integrity
- Connection integrity with recovery
- Connection integrity without recovery
- Selective field connection integrity
- Connectionless integrity
- Selective field connectionless integrity
- Non-repudiation
- Non-repudiation with proof of origin
- Non-repudiation with proof of delivery
Security Mechanisms
According to the Internet Security Glossary Version 2 (RFC 4949), a security mechanism is “A method or process (or a device incorporating it) that can be used in a system to implement a security service that is provided by or within the system”.
Some examples are authentication exchange, checksum, digital signature, encryption, and traffic padding.
Fund below is a summary of the security mechanisms described in the OSI security architecture:
- Specific Security Mechanisms
- Encipherment
- Digital Signature mechanisms
- Access Control
- Data Integrity
- Authentication Exchange
- Traffic Padding
- Routing Control
- Notarization
- Pervasive Security Mechanisms
- Trusted Functionality
- Security Label
- Event Detection
- Security Audit Trail
- Security Recovery
Security services and mechanisms and the OSI Reference Model
As you should know by now, the OSI Reference Model provides standardization for data networking. You can find a brief overview and the OSI layers in this post. The layers are important because they establish the way that communication is implemented in a network environment.
Find below a table that shows in which OSI layer (s) each service can be provided.
| Security Service | Layer | Mechanisms to provide the security service |
| Peer entity authentication | 3, 4 and 7 | authentication information transferred between application entities, protected by presentation or lower layer encipherment mechanisms |
| Data origin authentication | 3, 4 and 7 | supported by using signature mechanisms or lower layer encipherment mechanisms |
| Access control service | 3, 4 and 7 | the ability to communicate with specific systems or remote application entities may be provided by a combination of access control mechanisms in the application layer and lower layers |
| Connection Confidentiality | 1, 2, 3, 4, 6 and 7 | can be supported by using a lower layer encipherment mechanism |
| Connectionless Confidentiality | 2, 3, 4, 6 and 7 | can be supported by using a lower layer encipherment mechanism |
| Selective field confidentiality | 6 and 7 | can be supported by using an encipherment mechanism at the presentation layer |
| Traffic flow confidentiality | 1, 3 and 7 | can be supported by the use of a traffic padding mechanism at the application layer in conjunction with a confidentiality service at a lower layer |
| Connection integrity with recovery | 4 and 7 | can be supported using a lower layer data integrity mechanism (sometimes in conjunction with an encipherment mechanism) |
| Connection integrity without recovery | 3, 4 and 7 | can be supported using a lower layer data integrity mechanism (sometimes in conjunction with an encipherment mechanism) |
| Selective field connection integrity | 7 | can be supported using a data integrity mechanism (sometimes in conjunction with an encipherment mechanism) at the presentation layer |
| Connectionless integrity | 3, 4 and 7 | can be supported using a lower layer data integrity mechanism (sometimes in conjunction with an encipherment mechanism) |
| Selective field connectionless integrity | 7 | can be supported using a data integrity mechanism (sometimes in conjunction with an encipherment mechanism) at the presentation layer |
| Non-repudiation Origin | 7 | can be supported by an appropriate combination of signature and lower layer data integrity mechanisms possibly in conjunction with third-party notaries |
| Non-repudiation Delivery | 7 | can be supported by an appropriate combination of signature and lower layer data integrity mechanisms possibly in conjunction with third-party notaries |
Notice that the application process may provide all the security services using the same mechanisms as recommended by OSI Security Architecture.
The OSI Security Architecture is considered an efficient way to assess the security needs of an organization. These security needs can be specified by using the CIA Triad.
Related posts:
