Modern Cryptography uses complex algorithms to encrypt information. These algorithms can be classified as symmetric and asymmetric. AES and GOST are two of the modern symmetric cryptographic algorithms.
You can find an explanation of symmetric and asymmetric algorithms in the article General Concepts to study Cryptography.
The security principles of modern cryptography symmetric algorithms are similar to those of classical cryptography. Through substitutions and permutations, a high level of diffusion and confusion is achieved in the encrypted message. When high levels of confusion and diffusion are achieved in the encrypted message, it will have a random appearance and makes cryptanalysis difficult.
Bit-level calculation operations are used in modern symmetric algorithms since their execution speed by current microprocessors is very high. One of the most used is the XOR. This function has the characteristic that the output is the same size as the input and makes it easy to manage the memory space required to use it.
Modern symmetric algorithms are grouped into two large families. Stream cyphers and block cyphers.
Stream cyphers
These types of cyphers perform an XOR operation on the bits of the message to be encrypted and a pseudo-random sequence1. The sequence is generated from a random key or “seed” and a process that allows reusing and combining the bits to increase their size. Then, when performing an XOR between the message and the pseudo-random sequence, the result is visibly random and therefore difficult to cryptanalysis.
The complex task, in this case, is to generate the pseudo-random sequence that is used to encrypt the message. One way of doing this is to use feedback registers, which perform mathematical operations between the bits already generated from the seed and new bits are obtained for encryption.
These generating records must-have design properties that prevent the seed from being deduced from the generated sequence. If you don’t know the seed, it should not be possible to define the next bits that are going to be generated.
Block cyphers
Block cyphers divide the message to be encrypted into several bit blocks. Then, each block is encrypted separately. Dividing the message into blocks and encrypting each one independently makes it possible to encrypt any message regardless of size.
Depending on the algorithm we use, the size of the block to be encrypted can vary. In encryption, all the blocks will be of the same size. If the message length is not exactly a multiple of the block size, then the last block is padded to cover the specified size. This can cause the encrypted message to be slightly larger than the original message.
Comparison between stream and block cyphers
Stream cyphers require little processing power and are useful when the communication channel can cause loss of information or interference. Its main limitation is that with one seed, we can encrypt a limited size message.
In block cyphers, if a block is damaged or modified, the original message cannot be obtained, while in stream cyphers, only the affected bit sequence is lost. If you have the key, then it is possible to reconstruct the rest of the message.
Stream cyphers are used mainly in hardware components with low memory resources or in communications with a lot of interference and risk of information loss.
Block cyphers require higher processing power and mainly RAM. Modern computers generally have the necessary requirements for the execution of this type of algorithms. Their main advantage is that they allow large volumes of data to be encrypted with a small key. These algorithms are the most used nowadays.
Summary
Find below a summary of the two types of algorithms.
| Criteria | Stream cypher | Block cypher |
| Hardware requirement | Lower | Higher |
| Size of the message to encrypt | Limited by the key size | Unlimited |
| Behaviour when loss of information can occur | It is possible to decrypt a part of the message | Decryption is not possible |
In the following sections, I will explain the operation of 2 block encryption algorithms that are currently considered safe and represent international encryption standards. You will see the basis of their safety and how they should be used.
In general, for the design of a block cypher, we must consider 4 functions:
- Initial transformation: transformations to randomize the text to be encrypted and hide data blocks that contain only 0 or 1.
- Cryptographic function iterated N times: We apply a complex non-linear function which result will depend on the data and the key. It can be made up of a very complicated operation or many simple operations. This function is the core of the cypher.
- Final transformation: Used to make encryption and decryption operations symmetric. That allows the same algorithm to be used for encryption and decryption.
- Key expansion algorithm: This function allows to convert the key entered into the algorithm into a larger key. This key is divided into a set of sub-keys that will be used in the different encryption rounds of the block.
AES cypher
Advanced Encryption Standard (AES) is the encryption standard established by the National Institute of Standards and Technology. This standard is also known by its original name Rijndael.
AES characteristics
The following are characteristics of AES:
· Variable key size: 128, 192, 256 bits.
· 4-byte (128-bit) text block size.
· Use S-boxes like DES.
· A variable number of rounds depending on the key length you are using.
How AES works?
In AES, we group data into two-dimensional arrays of bytes. We perform four transformations on bytes with specific purposes. Each of those transformations is repeated in each round of encryption.
Encryption features:
- ShiftRow. The bytes of the block to be encrypted are placed into a 2-dimensional array. The ShiftRow function rotates the rows by several positions defined in the algorithm. The number of rotations depends on the position of the row in the matrix.
- MixColumns. Multiply the bytes of the array within the Galois field by a given array.
- ByteSub (Byte substitution). It consists of the substitution of the Bytes applying “S-Box” (Substitution Box) in parallel. An “S-Box” is a function that has a defined mechanism to substitute a set of input bits for an output set of bits. It has a substitution matrix and certain rules. Starting from the input, the output bits are searched in the matrix. S-Box designs must meet optimal non-linearity properties.
- AddRounKey (Add the round key). It is an XOR between a ciphertext intermediate state and the round subkey.
Encrypted message security properties
- Diffusion: Met by executing the “ShiftRow” and “MixColumns” functions.
- Confusion: Achieved by executing the “ByteSub” function. Byte substitution has similar functions to symbol substitution in substitution algorithms. You can read more about it in this post.
- High dependence on the key: By executing the AddRounKey function, the encrypted message depends on both the original message and the key used to encrypt it.
AES rounds
The number of rounds in AES depends on the key size we are using.
When AES 256 is chosen, it means that the AES algorithm is being used with a 256-bit key. The larger the key size, the more secure the encryption, but it also requires more processing power, therefore it takes more time to complete the encryption.
AES allows several key lengths, so you can adapt it to your needs.
• 16 bytes (128 bits) = 10 rounds.
• 24 bytes (192 bits) = 12 rounds
• 32 byte (256 bits) = 16 rounds
AES encryption process
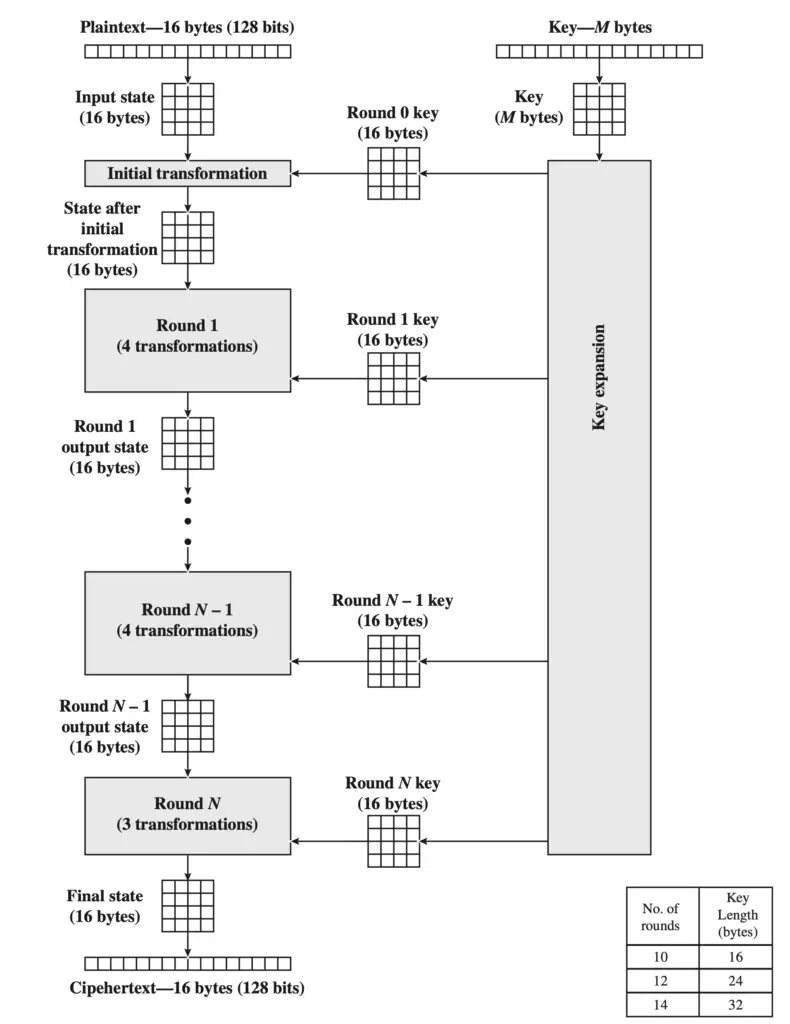
Steps for AES execution
From the key entered by the user, we execute a key expansion function to calculate the subkeys for each round of encryption.
Round 0 begins with the AddRounKey function between the first subkey and the block to be encrypted.
Then, we execute round 1 to the second last round, we execute the transformations on the block to be encrypted in the following order: ByteSub, ShiftRow, MixColumns and again AddRounKey with the next subkey.
The final round executes ByteSub, ShiftRow, AddRounKey.
At the end of the last round, we obtain an encrypted block.
The process is repeated for each block of bytes until the entire message is encrypted.
AES decryption
The decryption process is like the encryption one, but with the inverse of the functions used to encrypt.
Decryption operations:
1. InvShiftRow
2. InvMixColumns
3. InvByteSub
4. InvAddRounKey
GOST cypher
GOST is the standard for symmetric cryptography used by the Russian government.
Features of the GOST algorithm
- Key length 256 bits.
- 32 rounds of encryption.
- 11-step counterclockwise rotation.
- It is a Feistel type. This type of algorithm has the characteristic of dividing the block in half, working the two halves separately and then combining them.
- 8 S-Box.
Subkeys
1. The data block is divided into 2. Li = Right side and Ri left side where “i” is the number of the iteration.
2. Ri is added modulo 32 with the iteration subkey.
3. The bits of the output block are substituted using 8 S-boxes in parallel, similar to AES.
4. The output is rotated 11 positions to the left.
5. We use the resulting block in an XOR operation with the other half Li.
6. In the next iteration, the blocks are inverted, and the same process is carried out until reaching iteration 32.
When finished, the 2 halves are joined, and we obtain the encrypted block.
Encrypted message security properties
Diffusion: It is achieved by rotating the bits 11 positions to the left.
Confusion: It is achieved by substituting the bits in the S-boxes.
High dependence on the key: It is achieved with the sum modulo 32 between the bits of the subkey and the middle of the block in each of the iterations.
Comparison between GOST and AES
| Criteria | AES | GOST |
| Block size | 128 | 64 |
| Key size | 128,192, 256 | 256 |
| Rounds | 10, 12, 16 (key size dependant) | 32 |
Conclusions
The AES algorithm is more flexible in terms of the number of rounds and the length of the key. That makes it more adaptable to different hardware specifications. By using smaller key-size we can achieve the encryption faster. It requires fewer resources but is less secure. Increasing the key length increases its security but requires more processing power.
GOST algorithm is less flexible, it is designed to operate with the highest safety standards.
Currently, both AES and GOST, are considered secure using the 256-bit key length. Using it with a longer key length can make it very slow to execute, and with a shorter key length, it is not considered insecure.
There is software such as veracrypt, that allows you to combine several encryption algorithms. That is a good practice to protect your information.
If the software you are using does not support multiple layers of encryption, then you can combine multiple tools. Encrypt first with one tool using one algorithm and encrypt the result with another using another algorithm. To decrypt, you must perform the process in reverse order.
Apart from the algorithms explained, others such as MARS, RC6, Serpent and Twofish can also be used, but always with a key size of not smaller than 256 bits.

