Informally, insecure ports are ports that do not encrypt the communication that occurs through that port.
Ports in a computer are a virtual place where network connections start and end. The ports are virtual as they are software created and managed by your operating system.
This means you can configure them from your operating system. Also, you can close or open them according to your needs.
Some network services are associated with a port. Some ports encrypt the data that passes through, and some don’t.
Insecure ports are considered those that do not encrypt the data. Notice that this does not make the ports that encrypt data completely secure, as they often have vulnerabilities.
See below a list of ports that do not encrypt the data and therefore are considered insecure.
Table of Contents
Port 21
File Transfer Protocol (FTP) uses port 21 to transfer files from one computer to another. When using this protocol, you are sending the user and password in plaintext over the network.
Anyone that is “listening” to the communications from and to your computer, will be able to capture your login details and therefore, gain unauthorized access to the data.
Port 23
This port is the one used for a telnet connection.
Telnet is a software that allows you to connect remotely to a computer, and execute commands on that computer.
All the communication using telnet on the port 23 is unencrypted. This means that an attacker that is listening to the communication channel you are using, will get your login details and will gain unauthorized access to the remote computer you are connecting.
Even worse, if you are using your domain credentials, then the attacker can get unauthorized access to all the resources you have access to in the network.
Port 25
Simple Mail Transfer Protocol (SMPT) is used to send emails.
The data transmitted using this protocol, which uses port 25, is not encrypted.
The result? Someone “sniffing” on your network, can get access to the messages you are sending.
Imagine you are sending an email that contains proprietary sensible information about the business, and it gets into the wrong hands. This is a situation where you definitely don’t want to be.
Port 53
Domain Name Service (DNS) is a service used to assign a name to your computer.
As we know, computers have an IP address, it can be IPv4 or IPv6. But it is easier for us humans to remember a name than a sequence of numbers.
It is easier to remember the name Microsoft.com than to remember the IP address 20.76.201.171. What do you think?
The information transmitted using this port is unencrypted and, therefore considered unsecure.
Port 80
The HTTP protocol is used mostly by web browsers to show you a web page or a web application.
The protocol is not secure as all the data that is sent is not encrypted. Therefore, anyone who is “listening” to the communication channel can get access to all the data.
Even though companies are working hard for not to use this protocol, some companies and individuals still use it. Some for no reason and others to get access to your private information, like passwords, credit card numbers, etc.
If you are browsing the internet and come across a website that uses HTTP, you should get out of it. It is not secure to interact with such websites.
Port 143
Internet Message Access Protocol (IMAP) is the protocol used to retrieve emails from a server.
This protocol is also not secure as the data transmitted is not encrypted. Therefore, it is susceptible to network sniffing.
Port 445
Server Message Block (SMB) is used by several versions of Windows Operating System to access files over a network.
This service transmits the data unencrypted. So, if someone is “listening” in the network, can get access to files even though it does not have the credentials to get the files by himself/herself.
Port 389
The Lightweight Directory Access Protocol (LDAP) is an open, vendor-neutral, industry-standard application protocol for accessing and maintaining distributed directory information services over an Internet Protocol (IP) network. Directory services play an important role in developing intranet and Internet applications by allowing the sharing of information about users, systems, networks, services, and applications throughout the network. Source.
The data transmitted using this protocol is not encrypted. Therefore, it is susceptible to network sniffing and manipulation attacks like a Masquerade attack or MITM attack.
Here is a picture of the general form for attacks in insecure networks.
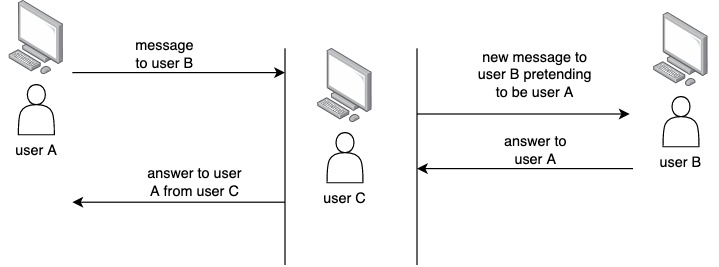
Apart from this type of attack, common scenarios involve stealing information or gaining unauthorized access to network resources.
Next, you can read about some of the ports that are secure in your computer.

