Contributed by Mulanduleni Niilungu.
Combining different blockchain networks is of great interest because it can be used to give new and enhanced services by communicating several blockchain networks. For that purpose, we can use CCIP to securely create services that use more than one blockchain network.
Table of Contents
- Introduction
- What is CCIP
- Benefits blockchain can achieve when using CCIP
- Some disadvantages Cross-chain
- Architecture Considerations
- How cryptography is applied in CCIP
- References
Introduction
Blockchain networks rely on their own communities and norms for governance because they are decentralized. The network’s infrastructure is built to support a stand-alone environment, even though data saved on the chain is completely visible (Ou, et al., 2022).
Blockchain technology has proven to be effective in some scenarios, it has a siloed nature, preventing the progress of decentralized finance (DeFi) and other decentralized applications (Decrypt, 2021).
Blockchain interoperability refers to a wide range of approaches that allow several blockchains to communicate, share digital assets and data, and perform more efficiently together.
This article will adopt the BI-recommended definition by Lohachab et al., (2021) “An interoperable blockchain infrastructure that can be considered as a composition of autonomous blockchain networks, where each network can be depicted as a distributed ledger of data, in which data can be operated among heterogeneous unconnected blockchain networks, and where data ledger can be accessed by validated foreign data”.
What is CCIP
Cross-Chain Interoperability Protocol (CCIP) is a new open-source standard for cross-chain communication. CCIP aims to establish a universal connection between hundreds of blockchain networks, both private and public, unlocking isolated tokens and empowering cross-chain applications for all on-chain ecosystems (Chainlink, 2021).
Furthermore, CCIP provides smart contract developers with a generalized, compute-enabled infrastructure for transferring data and smart contract commands across blockchain networks (Chainlink, 2022).
CCIP will underpin a variety of cross-chain services, such as the Chainlink Programmable Token Bridge, which will empower users to move their tokens across any blockchain network in a highly secure, scalable, and cost-efficient manner (Chan, et al., 2021).
A video by Breidenbach (2022) discussed several use-case examples of how interoperability can be achieved:
(1) Trading /trade assets: A cross-chain swap enables token exchanges between blockchains without involving a middleman (like an exchange service).
(2) Collateral uses funds deposited on one chain as collateral to borrow against another chain. The capacity to lend out cryptocurrency and earn interest in the form of cryptocurrency incentives is made available through cryptocurrency lending platforms for investors. Lending platforms first gained traction in 2020, and they now have billions of dollars in total value locked on numerous platforms.
(3) Decentralized lending has grown to play a crucial role in the development of the on-chain financial system since the tremendous expansion of DeFi activity and innovation in the middle of 2020.
(4) Cross-chain governance automatically disseminates governance decisions across many chains.
(5) New Kinds of dApps take advantage of network effects on Ethereum Mainnet while harnessing computing and storage on other chains.
(6) Enterprise workflows decentralized validation technology to reduce risk in cross-chain, multiparty middleware communications.
Benefits blockchain can achieve when using CCIP
1- Decentralized and trust-minimized
All cross-chain token transactions will be cryptographically signed and validated by hundreds of independent, Sybil-attacks resistant Chainlink oracle nodes from top node providers, powered by Chainlink’s improved off-chain reporting protocol (OCR 2.0), minimizing any single point of failure (Chainlink, 2022).
2- Compute-enabled
Enables the development of new cross-chain token-based applications by allowing developers to create programs (such as wallets) that can transfer tokens and start programmable activities on the destination chain. The ERC-20 tokens can be created, burned, locked, and unlocked via the Programmable Token Bridge (Chainlink, 2022).
3- Highly secure with Anti-Fraud Network
Secured by a separate anti-fraud network that proactively scans blockchain networks for vulnerabilities (such as inaccurate or excessive fund transfers) and takes preventative action when malicious activity is discovered (such as stopping fund transfers) in a way that minimizes trust (Chainlink, 2022).
4- Universal and chain-agnostic
An all-encompassing interface that enables token transfers to any blockchain network across EVM and non-EVM chains, removing the need for developers to create separate bridges for intra-chain communication (Chainlink, 2022).
5- Multi-Chain ecosystem
Giving developers a standardized method for creating cross-chain apps, safely expanding the multi-chain ecosystem, and enabling secure token transfers between various blockchain settings would greatly increase the utility of user tokens (Chainlink, 2022).
Some disadvantages Cross-chain
Firstly, Cross-chain protocols are inherently complex. A multi-chain smart contract is no longer a single, cohesive program because each time the code for the contract is deployed on a different blockchain network, a brand-new copy of the application is created.
Instead, there is little to no compatibility between contract deployments on different blockchain systems, and each one manages its internal data (such as tracking account balances) independently. Although users can access a copy of the program on the network of their choice, the user experience may vary depending on the chain (Chainlink, 2022).
Thirdly, According to Chainalysis (2022), there have been cross-chain bridge breaches that have resulted in the theft of $2 billion in bitcoin, the majority of which was taken in 2022 alone. 69% of the total funds stolen in 2022 to date have been obtained through attacks on bridges.
Therefore, Cross-chain protocols present a large attack surface as Cross-chain bridges attract more hackers as more value passes over them since they are more alluring to hackers, adversaries are sophisticated, and include state-level actors (Breidenbach, 2022).
Architecture Considerations
This protocol may be used on decentralized oracle networks like Chainlink and has important additional features like the Anti-Fraud Network to demonstrate the accuracy and dependability of transactions (Chainlink, 2022).
The protocol offers end-to-end Security coupled with several features such as each component being hardened. The ability of the protocol to minimize the risk of a single-point failure, stronger defense-in-depth, and ensuring that safety is more important than liveness.
Also, the protocol promotes interoperability by ensuring that it connects contracts on heterogeneous chains and Chainlink believes that by forward-looking.
The ecosystem will keep evolving, therefore, it is empirical that CCIP evolves alongside (Breidenbach, 2022).
Architecture Deep Dive
A video by Breidenbach (2022) discussed several terminologies that one first needs to understand before a deep dive into the architecture.
- CCIP enables a sender on a source chain to send a message to a receiver on a destination chain, Sender: A smart contract, Source Chain: the blockchain the sender contract is executing on.
- Message: data and tokens
- Receiver: a smart contract
- Destination Chain: the blockchain the receiver contract is executing on.
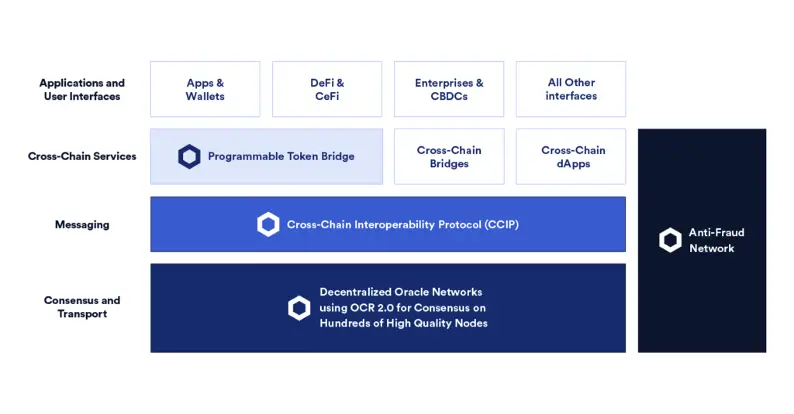
User Interfaces
The APIs at the top of the technological stack allow users to connect to the Chainlink Programmable Token Bridge or other bridge implementations and begin moving their tokens across blockchain environments.
It is worth noting that new and current ecosystem projects can deploy their interface without restriction.
Established wallets, aggregators, applications, exchanges, and a wide range of user-facing businesses that wish to provide a gateway to the multi-chain ecosystem are examples of this (Chainlink, 2021).
Programmable Token Bridge
The Programmable Token Bridge is a reference bridge implementation based on the CCIP that allows developers to create cross-chain apps that transport current tokens over any blockchain effortlessly and safely.
It is a unified bridge system in which various bridge connections between chains are secured by distinct node committees to distribute security while retaining universal interoperability via routing contracts. T
he Programmable Token Bridge will support existing token standards, allowing liquid assets to be utilized quickly within various smart contract ecosystems. In addition to using high-quality node operators and a decentralized architecture, other safety procedures will be developed, such as time-based flow limitations to reduce downside risk during black swan events, the parameters of which can be handled by much bigger DONs (Chainlink, 2021).
The Programmable Token Bridge is compute-enabled, allowing users and smart contracts to input not only tokens but also commands to the bridge, which will then perform bespoke logic surrounding how it interacts with other blockchains.
Users do not need to understand how to use other blockchains; simply submit instructions to the bridge on how they want to interact with other chains, and the bridge will transport the tokens cross-chain and deploy them in smart contracts on the target chain in an atomic transaction. As a result, a user can remain on their preferred blockchain while still benefiting from smart contract ecosystems on other blockchain networks.
The Programmable Token Bridge enables sophisticated hybrid smart contract use cases like cross-chain yield aggregators and collateralized loans, among others. Importantly, the Programmable Token Bridge is only one example of a reference implementation produced by Chainlink Labs; any third-party bridge application can be readily built by independent development teams interested in using the security and functionality of CCIP (Chainlink, 2021).
Cross-Chain Interoperability Protocol (CCIP)
The CCIP is intended to rapidly extend what developers may build by allowing the usage of smart contracts from across the blockchain industry.
CCIP enables fully original cross-chain applications that can use numerous smart contracts at the same time, as well as take advantage of individual chains’ or assets’ unique qualities.
The introduction of the CCIP is designed to rapidly expand what developers can build by enabling the use of smart contracts from all over the blockchain industry.
CCIP enables completely novel cross-chain applications that can utilize multiple smart contracts at the same time, as well as take advantage of the unique properties of specific chains or the assets on those chains.
This opens the door to a slew of new cross-chain apps and protocols that can exploit one blockchain’s scalable compute, another’s liquidity, and a third’s security for governance, resulting in a single application that leverages the expansive capabilities of a cross-chain meta-layer.
The Cross-Chain Interoperability Protocol (CCIP) is a new worldwide standard that will be used to power all blockchain interoperability, token transfer, and sophisticated cross-chain applications. CCIP, like TCP/IP, provides a global open-source standard for how all blockchains interoperate with one another, creating a new world of cross-chain smart contracts (Breidenbach, 2022).
Network Infrastructure
Chainlink’s cross-chain technology stack will be driven by decentralized networks of independent, well-known oracle node operators. Chainlink nodes will use the OCR 2.0 client to obtain off-chain consensus on cross-chain transactions securely and cost-effectively. OCR 2.0 eliminates any single point of failure and enables scaling to hundreds of independent node operators without significantly increasing on-chain gas prices. Importantly, the report will include the signature of each Oracle node that answered, providing accountability and a trail that may be leveraged to deploy trust minimization.
Anti-Fraud Network
Security and fraud prevention are critical components for cross-chain services that attempt to directly safeguard high-value contracts. To that purpose, the Anti-Fraud Network is a freshly designed risk management solution never previously seen in the blockchain sector. The Anti-Fraud Network is made up of decentralized Oracle networks that solely monitor CCIP services for fraudulent activities that could result in financial loss. In addition, to the node committees that are responsible for monitoring CCIP, the Anti-Fraud Network contains wholly separate committees of nodes, completely separating anti-fraud detection and cross-chain services (Chainlink, 2021).
When the system is working normally, the Anti-Fraud Network operates as a verification layer, submitting heartbeat checks regularly. If the Anti-Fraud Network’s heartbeat messages stop or any suspicious activity is detected, an emergency shutdown is automatically triggered to stop a specific cross-chain service. The pause protects customer cash from a hypothetical black swan incident impacting the service. While the Anti-Fraud Network will initially consist of high-quality Chainlink nodes that are independent of the CCIP services they protect, dApps that secure a large amount of value through a CCIP service can join the Anti-Fraud Network to provide greater guarantees to their users that any fraudulent activity will be detected and mitigated (Chainlink, 2021).
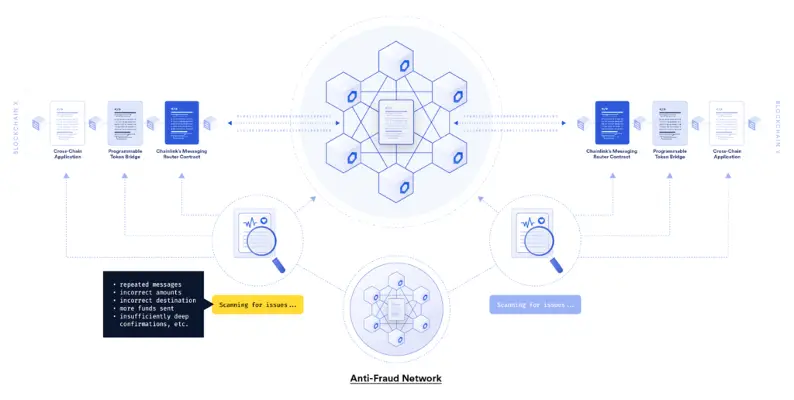
The Anti-Fraud Network is decentralized risk management and anti-fraud detection system that is often utilized when protecting high-value contracts. The Anti-Fraud Network transforms how risk is managed in cross-chain infrastructure by building a framework of checks and balances that separates duties and limits any single group’s influence over the functioning of CCIP services. Importantly, the network can scale and evolve in the future with additions such as AI for improved detection approaches (Chainlink, 2021).
How cryptography is applied in CCIP
1- Notary mechanism
The notary mechanism functions as a mediator between the mutually untrustworthy parties A and B in the notarial mechanism.
One of the main protocols of the notary mechanism, Interledger, enables financial transactions between two distinct blockchain systems by using “connectors,” or middlemen (Ou, et al., 2022).
2- Sidechain/ Relay Solutions
A sidechain is a blockchain that is tethered to the primary blockchain in two directions. Assets are transferred between the sidechain and the mainchain using a two-way peg connection.
A sidechain’s implementation may differ from the parent chain’s and it may operate independently.
The main purpose of a sidechain is to expand the functionality of the main blockchain or to increase its scalability.
On sidechains, transaction times are typically reduced (Alvi, et al, 2020).
3- Smart Contract Solutions
When a transaction between two parties occurs wholly or not at all, it is considered atomic. When two users utilizing separate blockchains seek to swap assets without the involvement of a trusted third party, they engage in atomic cross-chain trading.
This type of trade is also known as an atomic swap. Atomic swaps use hash-locks and time-locks to record transactions on both blockchains involved in trading without involving a third party.
Hashlocks and time-locks bind a recipient to permit transaction payment by generating cryptographic evidence within a specified time limit.
To eliminate counterparty risks, atomic swaps use Hashed TimeLock Contracts (HTLCs), which are smart contracts. Other interoperability solutions use atomic cross-chain transactions as well (Aleksieva, Valchanov, & Huliyan, 2020).
4- Hash-locking
Hash-locking, also known as hash time-lock contract, is a cross-chain technical solution that allows for comprehensive inter-chain asset exchange using hash-locks and time-locks without the use of trusted notaries.
During the implementation process, the initiator first chooses the secret value at random as the key for hash decryption, then hashes the secret value and provides the acquired hash value to the responder as the hash-locked public key.
The initiator and responder use the hash value to lock their digital assets in the smart contract and establish their time-locks (typically the initiator’s time lock is longer than the responder’s time-lock).
If both parties provide the secret value within the specified time, the assets locked in the contract will be successfully exchanged; otherwise, the assets locked in the contract will be recovered by the other party if either party fails to provide the secret value (the key for hash decryption) within the specified time.
The hash-locked atomic swap protocol assures that the total number of assets in the same chain remains unchanged, but its scope of usage is somewhat limited, and it can usually only be used for cross-chain asset exchange, not cross-chain asset transfer (Ou, et al., 2022).
Some users have minimum knowledge of CCIP, therefore some of the following questions are frequently asked.
- What is Blockchain Interoperability?
- Interoperability in Web3 – Why it Matters
- Name other Blockchain Interoperability Protocols apart from CCIP.
- How Does the Lisk Interoperability Solution Work?
- How to Build an Interoperable Blockchain?
The launch of CCIP is designed to dramatically broaden the scope of what developers can build on each blockchain. Cross-chain apps that use tokens on all chains simultaneously and take advantage of the particular qualities of certain networks or the applications and assets on those chains become possible (Chainlink, 2021).
This opens the door to a plethora of new cross-chain applications, such as cross-chain protocols that combine one blockchain’s scalable computation, another’s token diversity, a third’s storage, and a fourth’s settlement security to create a single hybrid smart contract application with superior functionalities.
References
Aleksieva, V., Valchanov, H., & Huliyan, A. (2020). Implementation of Smart Contracts based on Hyperledger Fabric Blockchain for the Purpose of Insurance Services. 2020 International Conference on Biomedical Innovations and Applications (BIA), 113-116. doi:10.1109/BIA50171.2020.9244500
Alvi, S. T., Uddin, M. N., Islam, L., & Ahamed, S. (2020). A Blockchain based Cost effective Digital Voting System using SideChain and Smart Contracts. 2020 11th International Conference on Electrical and Computer Engineering (ICECE), 467-470. doi:10.1109/ICECE51571.2020.9393081
Belchior, R., Vasconcelos, A., Guerreiro, S., & Correia, M. (2021). A Survey on Blockchain Interoperability: Past, Present, and Future Trends. ACM Computing Surveys, 54(8), 1-41. doi:https://doi-org.ezproxy.unam.edu.na/10.1145/3471140
Breidenbach, L. (2022, October 7). Architecting Secure Cross-Chain Infrastructure With CCIP. Retrieved from Youtube: https://www.youtube.com/watch?v=speIh3ctygM
Chainalysis. (2022, August 2). Vulnerabilities in Cross-chain Bridge Protocols Emerge as Top Security Risk. Retrieved from Chainalysis Web site: https://blog.chainalysis.com/reports/cross-chain-bridge-hacks-2022/
Chainlink. (2021, August 5). Introducing the Cross-Chain Interoperability Protocol (CCIP) for Decentralized Inter-Chain Messaging and Token Movements. Retrieved from Chainlink Web site: https://blog.chain.link/introducing-the-cross-chain-interoperability-protocol-ccip/
Chainlink. (2022). Build secure cross-chain applications quickly. Retrieved from Chainlink Web site: https://chain.link/cross-chain#programmable-token-bridge
Chainlink. (2022, January 19). Unlocking Cross-Chain Smart Contract Innovation With CCIP. Retrieved from Chainlink Web site: https://blog.chain.link/unlocking-cross-chain-smart-contract-innovation-with-ccip/
Chainlink. (2022, February 8). What Are Cross-Chain Smart Contracts? Retrieved from Chainlink Web site: https://blog.chain.link/cross-chain-smart-contracts/
Chan, B., Cachin, C., Breidenbach , L., Juels , A., Ellis , S., Coventry , A., . . . Zhang, F. (2021, April 15). Chainlink 2.0: Next Steps in the Evolution of Decentralized Oracle Networks. Retrieved October 7, 2022, from https://research.chain.link/whitepaper-v2.pdf
Decrypt. (2021, August 5). Retrieved from Chainlink Is Building a Billion-Dollar Bridge to a Multi-Chain World: https://decrypt.co/77668/chainlink-is-building-a-billion-dollar-bridge-to-a-multi-chain-world
Ou,, W., Huang, S., Zheng, J., Zhang, Q., Zeng, G., & Han, W. (2022). An overview on cross-chain: Mechanism, platforms, challenges and advances. Computer Networks, 218. doi:https://doi.org/10.1016/j.comnet.2022.109378.

