Contributed by Michael Shuufeni.
In this article, you will learn what are off-chain assets and how cryptography is applied to them.
Table of Contents
- What are Off-Chain Assets?
- How is cryptography applied to off-chain Assets?
- Proofs of Zero knowledge
- Hybrid smart contracts for content addressable storage.
- Advantages of Off-Chain Assets
- Disadvantages of Off-Chain Assets
- FAQs about Off-Chain Assets
- References
What are Off-Chain Assets?
The current architecture of the blockchain has four layers.
1- the hardware layer is concerned with distributed trusted hardware
2-Layer 0 is concerned with the network of the blockchains.
3- Layer 1 is concerned with the blockchain and the side chains and on-chain transactions
4- Layer 2 concerned with the protocols that happen outside the parent blockchain.
These layers make up the blockchain ecosystem and make it possible for the blockchain ecosystem to be scalable (Gudgeon, Moreno-Sanchez, Roos, McCorry, & Gervais, 2019).
Off-chain assets are transactions, outputs, inputs, and resources that happen outside the parent blockchain. Off-Chain Assets make it possible for blockchains to interact with the real world through the creation of secure channels that facilitates the movement of assets to and from the blockchain (Public Communications) to private communications.
How is cryptography applied to off-chain Assets?
Inside the blockchain are complex cryptographic computations that verify, secure, and calculate hashes of the blocks, transactions, and all other activities relating to the blockchain. The advancement in the development and scalability of the blockchain has seen the need to expand the application of cryptography to ensure that the off-chain products and activities are secure.
The advancement in the development and secure scalability of blockchain includes mechanisms such as off-chain computation that increases the usability of the blockchain. Some of these mechanisms are verifiable randomness, transaction ordering services, and smart contract automation. They are possible by new extensible computations provided by the Oracle Networks. The Oracle Networks do provide trust-reduced ways to off-chain computations.
To offer exhaustive security to off-chain assets, cryptography must be applied to the two most critical areas which are Off-Chain Data and Off-Chain Computations.
Off-Chain Data is a collection of real-world data sources that can provide scalability and extensibility of the blockchain. It is classified as Off-Chain Assets and these include financial data, weather data, gaming data, sports and logistics data, reserve data, identity data, and API data.
Off-chain computation and its protocols are computations carried out in the context of an off-chain computation protocol. It is specified through an off-chain program and a set of inputs protocol that allows the execution of computations on blockchain-external resources. These resources guarantee (under protocol assumptions) correctness of accepted on-chain results and that the results are available on the blockchain on protocol completion.
Off-Chain security and privacy cannot be achieved using the same cryptographic applications such as those of the parent blockchain and must therefore resort to cryptographic techniques such as proofs of Zero knowledge and hybrid smart contracts for content addressable Storage.
Proofs of Zero knowledge
The Zero Knowledge concept specifies that the blockchain and the off-chain reveal the correctness of the statement. To put this into the practice of verifiable computation, this strong property of zero knowledge makes it possible for the proving party to use private information since the proof does reveal nothing but the fact that the computation is correct. (Jacob, 2021) proposed a Zero Knowledge architecture that employs public key infrastructure to prove and verify the off-chain assets. In the implementation, two public keys are used one for proving and the other for verifying.
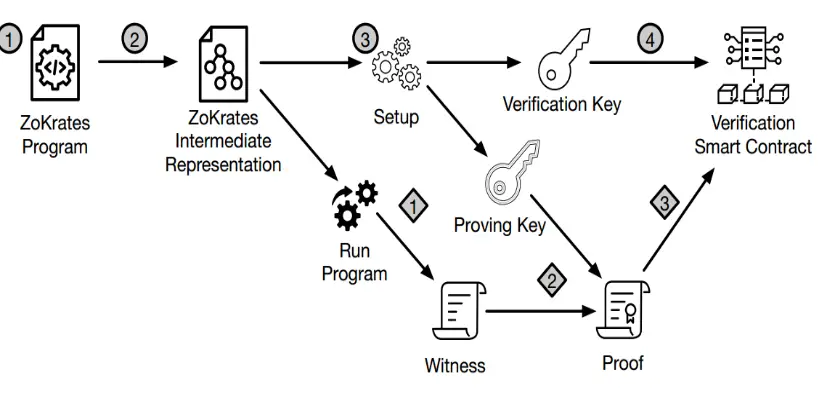
The ZoKrates program is used to perform the cryptographic computations of generating the verification key and the proving key. These keys can be used to encrypt the off-chain assets. It takes private compounds for execution and calculates their hashes using SHA256. The proving key together with the witness is used to generate the proof. The proof and verification key are used to create the verification smart contract.
Hybrid smart contracts for content addressable storage.
A smart contract encodes the rights of a piece of digital art. However, a piece of art would be
very costly to store on-chain due to its size. Instead, the file that encodes the piece of art is stored in a CAS system that identifies files by their hashes.
The file hash is stored in the smart contract, serving as a reference to the artwork. Clients can then retrieve the hash of the externally stored piece of art from the contract and use it to query the storage system. The result can then simply be hashed to verify its correctness. Cryptography is used to generate the hashes. These hashes can be viewed as unique identifiers and can be ported to the blockchain. The blockchain may not have the relative location and more information about the off-chain asset. The hashes of the off-chain assets are then used to create the smart contract that can be committed to the blockchain providing both privacy and security. (Kapsoulis, et al., 2020) stated that smart contacts, even though have been the gold standard for on-chain assets, can be expanded to cater to off-chain computability to provide hybrid services for on-chain and off-chain services.
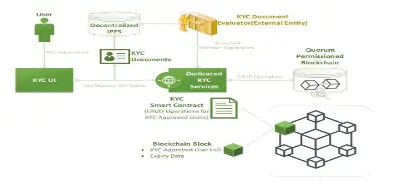
Figure two shows how a Decentralised Finance (DeFi) application, the Interplanetary File System (IPFS), is used to store the KYC documents that are then used to create the smart contract.
The smart contract has a unique identifier created using a hashing scheme such as the Modified SHA256.
That unique identifier is committed to the blockchain. It can be used to interact with the KYC services and no other information apart from the smart contract UID is revealed. MSHA256 can be used with smart contracts to which its tasks such as state channel where two different parties trust their off-chain agreement in place of the global blockchain agreement ( Perez, et al., 2020). The content addressable storage can form a decentralized oracle network that offers secure off-chain services that support the smart contract.
Advantages of Off-Chain Assets
Reduced transaction loads and costs: Off-chain assets reduce the transactional loads and costs because some transactions can be carried out off the blockchain freeing up the computational power for the blockchain to focus on crucial operations. Storing the Assets off-chain allows saves the costs usually incurred from storing larger assets on the blockchain.
Scaling of the blockchains: Off-chain assets makes it possible for the blockchain to scale to interact with the real world and provide more data sources for the blockchain to avail the advantages of the blockchain platform.
Increased number of transactions per second: Because off-chain assets transactions happen off the blockchain, it means the blockchain can carry out more blockchain-specific transactions. Therefore, increasing the transactions per second.
Disadvantages of Off-Chain Assets
Lack of formal security and privacy analysis: The security analysis requires off-chain operations to have their own independent security and privacy analysis and such security analysis and audit reports may not meet that of the blockchain provider. Hence, the acceptability to transact on the blockchain may be rejected.
Mixed cryptographic primitive off-chains: Off-Chain assets transactions may use different cryptographic schemes that the blockchain is unaware of, making such exchanges difficult and requiring the introduction of third-party computations and extensible virtual machines to handle the transactions.
FAQs about Off-Chain Assets
1- Who is responsible for securing the Off-Chain Assets?
This is an active research area. Securing Off-chain assets requires a multi-faced approach.
The security should not be too strict to lock out external communication and should not be too loose to accidentally reveal data that should be private.
Securing the off-chain assets is the responsibility of the party intending to commit the asset’s smart contract on the blockchain however guidance for smoother exchange should be provided by the blockchain platform advisory team.
References
Perez, M. R., Legaspi, J. B., Awa, K. A., Lagman, A. C., De Angel, R. M., & Adao, R. T. (2020). Design And Implementation Of Msha256 On Blockchain Using Content Addressable Storage Patterns. INTERNATIONAL JOURNAL OF SCIENTIFIC & TECHNOLOGY RESEARCH.
Groth, J. (2010). Short Pairing-Based Non-interactive Zero-Knowledge Arguments. Advances in Cryptology – ASIACRYPT 2010 (pp. 321–340). Berlin: Springer.
Gudgeon, L., Moreno-Sanchez, P., Roos, S., McCorry, P., & Gervais, A. (2019). SoK: Off The Chain Transactions. IACR Cryptol. ePrint Arch, 360.
Jacob, E. (2021). Scalable and Privacy-preserving Off-chain Computations. Berlin: Technischen Universität Berlin.
Kapsoulis, N., Psychas, A., Palaiokrassas, G., Marinakis, A., Litke , A., & Varvarigou, T. (2020). Know Your Customer (KYC) Implementation with Smart Contracts on a Privacy‐Oriented Decentralized Architecture. Future Internet, 41.
