A digital signature is a mechanism we can use to verify the authenticity of a message/document. It is usually needed in situations when there is no trust between sender and receiver.
We can use a digital signature to verify the author of the signature, to authenticate the content of the message. Also, third parties must be able to verify a signature, to resolve disputes.
A digital signature is not taking a picture of your signature and adding it to a document.
Two types of disputes that can be solved using digital signature are: the receiver can modify the message received and claim that it is the original one. The sender can say, at a later stage, that he/she did not send the message or that it was modified.
When using digital signatures, the two previous accusations are very easy to verify.
Table of Contents
- How does it work?
- Common scenarios
- What makes a digital signature secure?
- Digital signature providers
How does it work?
Bob wants to send an important message to Alice. But the two of them have worries about the message being modified or that Bob can say at a later stage that he didn’t send the message.
They decide to use a digital signature to solve the trust issue.
So, Bob writes the message (it can also be a document, the format does not matter). Then he uses a digital signature algorithm to create a signature. Each signature is dependent on the message being sent.
After that, both the message and the digital signature are sent to Alice. In this case, is not important the security of the medium because the main goal is to have proof that was Bob who signed the message.
Alice then uses a signature verification algorithm, if the signature is valid in can accept the message, knowing that the message came from Bob and that he cannot deny he signed it.
This process is described in the figure below.
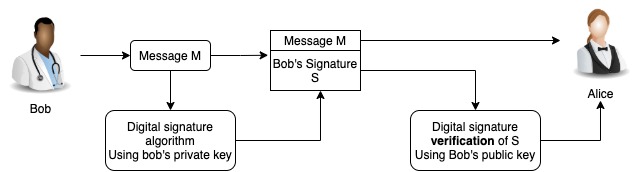
How do I create a digital signature?
A general approach to creating a digital signature is as follows:
- A hash is created from the message
- Then hash is encrypted with the sender private key producing a fixed-length value. This value is the signature
How is a digital signature verified?
When someone receives a digitally signed message, can verify the signature is as follows:
- Create a hash of the message
- Decrypt the signature using the sender’s public key
- If the two hash values match, then the signature is valid. Otherwise, the signature is not valid.
Common scenarios
There are two main scenarios where digital signatures are of particular significance.
The first one is on emails. Nowadays we are being the target of malicious people. One type of attack is sending emails that will ask for us to do something. Sometimes we don’t know how to verify the authenticity of the email, in other words, how to check if the person who apparently sent the message is indeed the one who send it.
We can use digital signatures to sign emails. Then we can be sure of who sent the email.
Another common scenario is to sign documents. In the corporative world, a lot of documents are signed daily. Then these documents are sent via courier to someone else, to take a specific action.
If we use a digital signature technology, then we won’t need to print messages and send them using a courier. We can just sign the document and send it via email.
What makes a digital signature secure?
The security of the mechanism lies in Cryptography.
The cryptographic hash functions that you use will guarantee many of the digital signature requirements to ensure the security of the mechanism.
Apart from that, we should take special care of the scheme we are going to use for the whole process of creating and validating the signature.
Some of the schemes are:
- Elgamal Digital Signature Scheme
- Schnorr Digital Signature Scheme
- NIST Digital Signature Algorithm (DSA)
Digital signature providers
There are many online digital signature providers. Find below three of them.
You can try how to digitally sign documents and messages using GpgFrontend. In this post, you can find an example and an explanation of how you can use it.
Related posts
OpenPGP: Encryption and digital signature using GpgFrontend
