This article explains what is OpenPGP and how to use it to encrypt and sign documents. You will understand how this standard works and the foundations of the security of hybrid cryptography systems.
What is PGP, OpenPGP and GPG?
Pretty Good Privacy (PGP) is an encryption system that combines symmetric and asymmetric algorithms for encryption and digital signature. It was originally designed and developed by Phil Zimmermann in 1991 in the USA.
One of the main characteristics is that first, the information is encrypted and digitally signed. Then, the message is sent over the communication channel and decrypted at the destination side.
The encryption and decryption process can happen without an active connection to a server since these operations are carried out with software that is installed on each user’s personal computer.
Because the laws in the US at the time prohibited the export of cryptographic software outside of their country, PGP could not be exported outside the USA. However, its source code could be studied and published as research articles. PGP software has been purchased by different companies varying the permissions and rights on it.
The IETF (Internet Engineering Task Force) was in charge of creating a free standard based on PGP called OpenPGP. It is described in the rfc4880 specification under the GPL license. This standard describes the specifications for developing software to encrypt and sign information based on the operation of PGP.
GNU Privacy Guard (GPG), which is also known as GnuPG, is a project that implements the OpenPGP standard. It contains several OpenPGP compatible software under a free software license. It has installers for several operating systems. The official website is http://gnupg.org. GPG can be installed from the official repositories of several Linux distributions. In the case of the Windows implementation, GPG4Win can be downloaded from this link.
OpenPGP example using GPG frontend
OpenPGP combines several symmetric and asymmetric cryptography algorithms for signing and encrypting information. The article “General concepts for studying cryptography” describes the characteristics that define both types of algorithms and explains how they can be combined to get the most out of each one.
In this example, I’ll use GPGfrontend as a tool with a graphic user interface to facilitate the process.
Key generation to use OpenPGP
Systems that use asymmetric algorithms to guarantee information security, encrypt the information using one key and decrypt the information using another key. That’s why each user must have a pair of keys. The public key is known by everyone that wants to communicate with the user (the owner of the pair of keys), and the private key is only known by one user (the owner of the key).
So, before being able to use OpenPGP, each user must create their public and private key.
This can be done using the GPGfrontend tool.
First, click the option Manage Keys from the toolbar.
Then click create a New Keypair.
Now it is time to add some personal information.
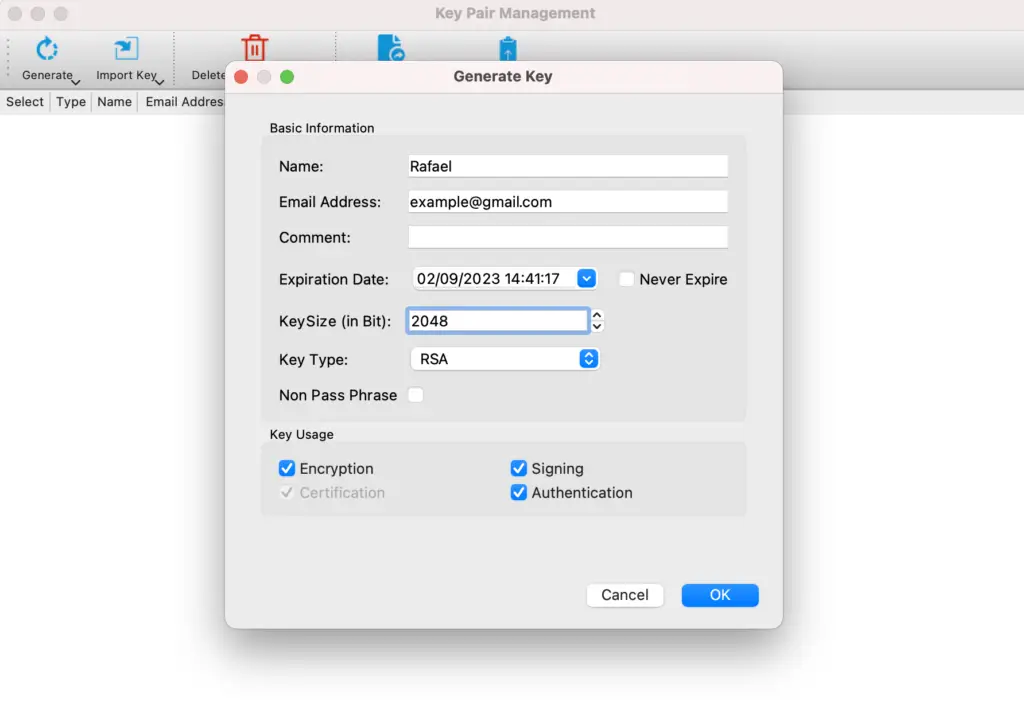
In this window, you can change the key size and the key type. Also, you can specify how you intend to use the key.
After that, your new key will appear on the main window (see on the right side).
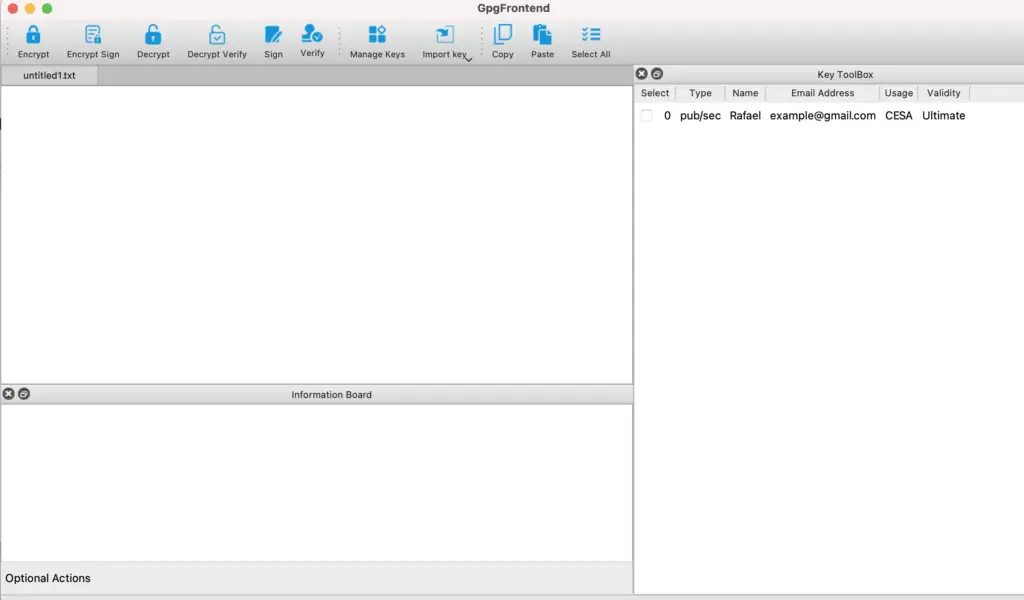
Asymmetric key pairs are considered “long-lasting keys”. It is recommended that you renew the key every 2 years unless a problem occurs that requires them to be renewed earlier.
I also recommend protecting the key with a password. The software offers this option and it will ask you for a “pass phrase” every time you want to encrypt or sign a message.
Public key exchange
Remember that each user must have the public key of the person to whom they want to send the information. When encrypting using PGP, GPG, OpenPGP or any other “hybrid cryptography” system ( which is how this type of system is named), you must choose for whom you want to encrypt the information and only that person can decrypt it.
To do that, it is necessary to have the digital certificate of that person in the list of recipients of the software that is being used. A certificate contains the information of a user and the public key of it. Having the digital certificate, the information destined for that person is encrypted and sent using a communication channel, such as mail.
The person who receives the encrypted file must also have the certificate of the person who sent it to be able to verify the signature. To publish and share these keys, public key repositories can be used where users’ public keys are shared. There are also certificate revocation lists where certificates or public keys that have been revoked for some reason will appear in a list.
If the two people know each other, they can simply send the public key by email and add it to the list of public keys of the application. In this way, each user has a list of certificates of the people with whom they wish to communicate.
You can send your public key by exporting it to a file as follows.
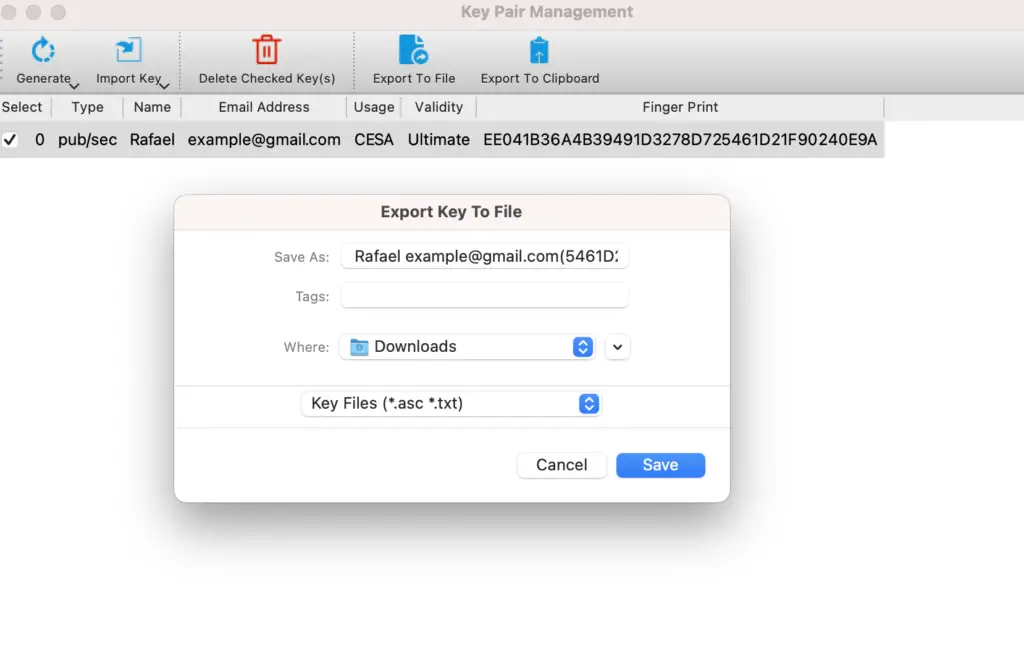
Following a similar procedure, you can import the public key of the person you want to send the message to.
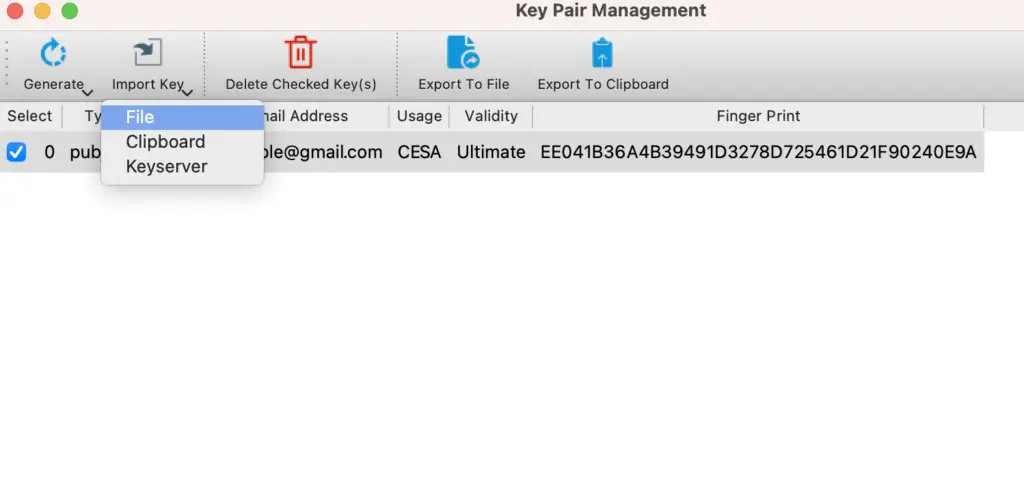
Encryption and digital signature
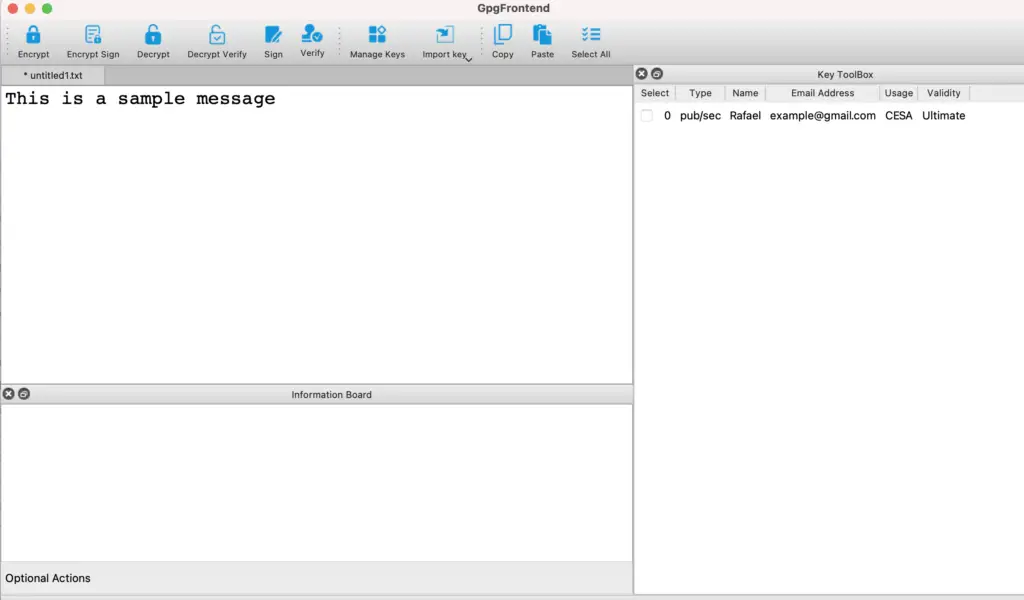
After the two users exchanged the digital certificates, the encryption process is very simple.
You write your message and use the options encrypt/decrypt or sign/verify accordingly from the toolbar.
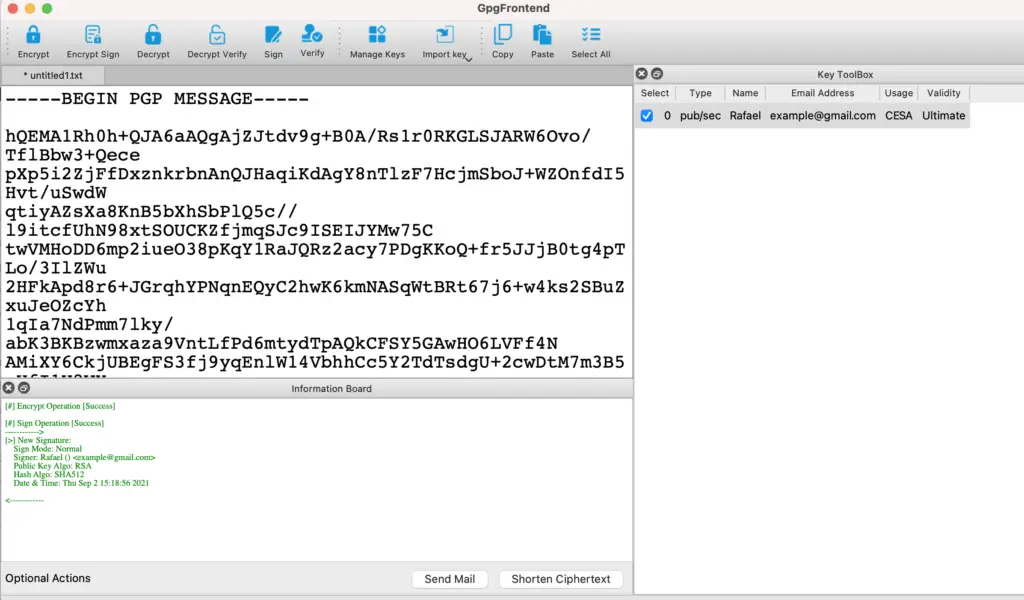
For instance, after an encrypt and sign operation, you will see something like this:
Decrypt and/or verify a message
Once you have an encrypted and/or signed message, then you can decrypt it or verify using the same tool.
See below an example of how you can decrypt and verify the message, using the same interface. Notice the options on the toolbar and the key that is selected on the “Key ToolBox”.
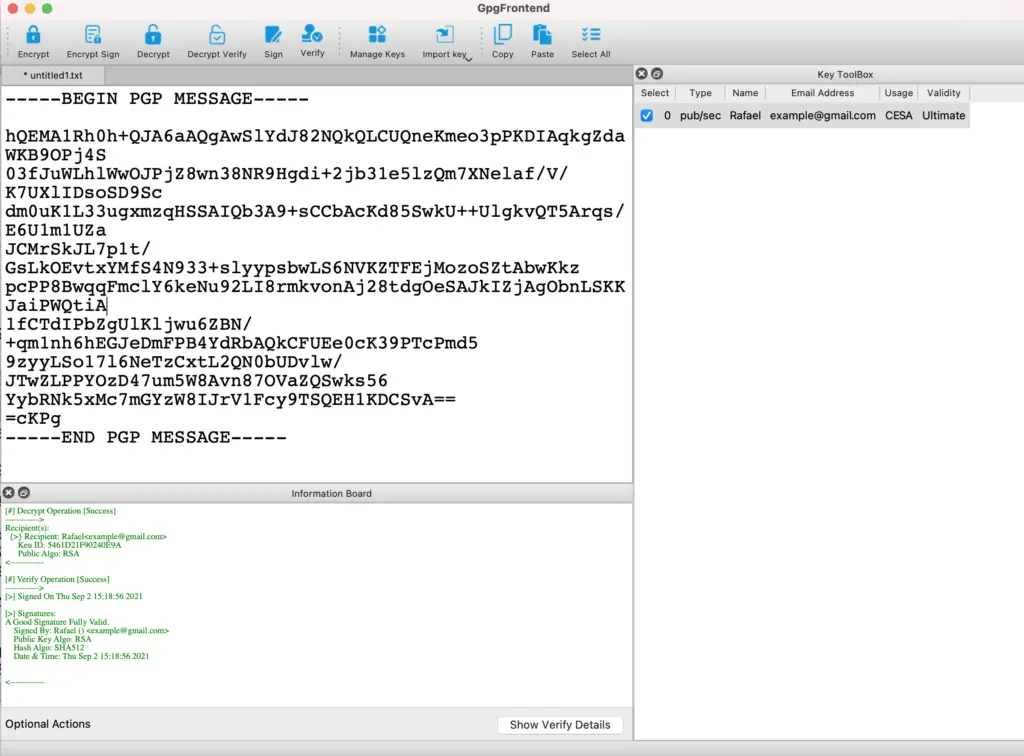
Notice the message on green.
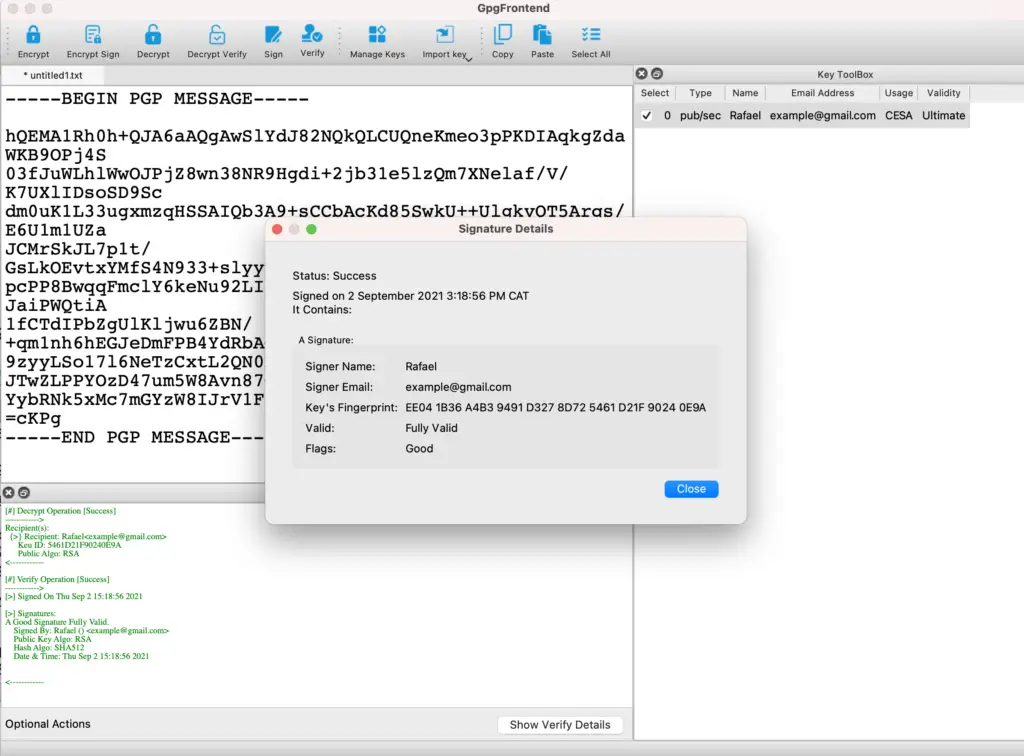
If you want to see more details of the verification, click on the button “Show Verify Details” at the bottom of the window. Then you will the following:
How OpenGPG works internally
The rfc4880 describes in detail the parameters for the OpenPGP implementation, algorithms, messages and requirements.
I’ll explain below how it works using a high-level view (not in detail).
OpenPGP sets the standard for the implementation of hybrid cryptography systems and is released under the GPL. Hybrid cryptography systems combine symmetric and asymmetric cryptography algorithms, and hashing functions to encrypt and sign the content that you want to protect. In the article “General concepts for studying cryptography” the operation of these algorithms is explained in a general way.
In the article “AES and GOST: Modern symmetric cryptography” and also in this link, I explain the principles of symmetric cryptography.
Example
According to the specification rfc4880, when user A wants to send a message to user B, the following operations must be performed.
A: write the message in plain text (M).
It then generates a one-time secret key (S) for M.
The secret key is a random value of a defined length generated by the cryptographic software depending on the symmetric encryption algorithm. Then, using a block encryption algorithm and the secret key, the message is encrypted.
A: encrypts M with a symmetric algorithm using the key S obtaining the encrypted message (Mc).
Encrypts the key S with an asymmetric algorithm using the public key of B obtaining (Sb).
Calculate the hash (H) file that has the encrypted message Mc and the key Sb.
It signs the hash H with his private key obtaining (Hf).
Send file (F) containing Mc, Hf and Sb.
With this information, the receiver can decrypt the secret key he received with his private key, since it was encrypted with his public key and, only he can decrypt it. Then, the receiver uses the public key of the issuer to verify the signature that is made to the Hash Hf and verifies that it is authentic. With the hash, the receiver checks that the encryption has not been modified. If everything is in order, then you can use the secret key you received to decrypt the message.
Compression algorithm
In this type of system, it is possible to use a compression algorithm to make the file be sent as small as possible. In rfc4880 this topic is mentioned but there is no description of the algorithm. It is recommended that the compression algorithm is used after the file is encrypted. The compression and decompression process can cause errors and affect the decryption of the file.
If you use a compression algorithm after the file has been encrypted, the compression is not efficient. Compression algorithms are based on finding patterns in the file to be compressed and replacing them with patterns that use less space. Then, to decompress a file it follows the inverse process. One of the objectives of the encryption algorithms is that the result has no patterns and thus make cryptanalysis difficult.
If a file is encrypted and then compressed, the size will be practically the same since it must not have patterns that make it possible to compress. If an encrypted file has a high degree of compression, then the encryption algorithm will probably need to be revised.
Summary of how hybrid cryptography systems work
Hybrid cryptography systems such as GPG use the potentialities of different types of algorithms to encrypt and sign messages. Symmetric algorithms are used to encrypt content because they are fast to encrypt and decrypt large volumes of data. The problem they present is that they use the same key to encrypt and decrypt. Therefore, the key is secret, and it is a problem to distribute that key. This problem is addressed by using asymmetric algorithms since they have a public and a private key. Distributing the public key is not a problem because anyone can know it. The problem is that they are slow and only efficient at encrypting small volumes of data.
For this reason, in OpenPGP, symmetric algorithms are used to encrypt the information and asymmetric algorithms to encrypt the key used to protect the information. That is, to exchange the keys. For the digital signature, a hash function is used, and the hash is signed since it is generally much smaller than the original message. In principle, if the hash of a message is signed, it is equivalent to signing the original message. The article “Cryptographic Hash Functions and HMAC” describes how hash functions work.
Although in theory, hybrid systems are complex, there are tools such as GPGfrontend and Kleopatra, that facilitate their use since it is only necessary to have basic notions of cryptography for their use. This type of system encrypts the information before sending it, so the user does not have to trust an external entity to protect their data.
