A Key Distribution Center is the way to automatically distribute keys to support arbitrary connections between pairs of users. The users can be a computer, a process or applications. Each user shares a unique key with the KDC, known as the master key.
To understand the use of a KDC we need to understand what the meaning of key hierarchy is.
Table of Contents
Key hierarchies
To use a KDC, we need a minimum of two-level key hierarchy.
The master key is used to identify the user and, the second key is used to encrypt the communication between the two users. This second key is usually known as the session key.
The session key is encrypted using the master key and it is then sent to the clients for an end-to-end encrypted connection.
Each session will have a different key. In this way, we are adding an extra layer of protection because all the traffic is encrypted using different keys.
So, if an attacker gets one key, it won’t be able to decrypt all the messages, only those messages encrypted with the specific key.
Hierarchical key control
In some cases, it will be important to have several KDCs when the number of users is large. The way to implement is assigning certain areas or IP ranges/networks to each KDC, so the keys are distributed within the area of the specific KDC.
If two users in a different area or under different KDCs need to communicate, then the request goes to a KDC in a higher hierarchical level, and this one is responsible to share the session key between the two users.
Drawback of a KDC
The main drawback of a KDC is that the KDC must be trusted. Also, it must be protected at all levels. If the security of the KDC is compromised all messages can be discovered easily.
One way to fight this drawback is using a decentralized approach to key distribution. Although not practical in large networks, can be of use in a local network.
KDC example
As an example of a KDC, we can mention Kerberos.
Kerberos is an authentication service that was developed at MIT. There is plenty of documentation on its website for you to see how to install it, configure it, etc. The documentation is also organized for users, administrators, etc.
The problem that Kerberos address is to authenticate access request by users in a network to different servers.
Notice that the main problem arises when we have many users that need access to several services distributed on different servers.
In this case, Kerberos acts like a KDC, creating session keys to establish secure connections between users and services.
Kerberos realm
Considering the problem that Kerberos addressed, described in the previous section, we can state that a Kerberos environment has the following components: a server, clients and services. The server has the users’ master key, as per KDC description and the services are registered in the Kerberos server.
This environment is known as a Kerberos realm.
When you have different networks, for instance, from different companies, you usually will have more than one Kerberos realm.
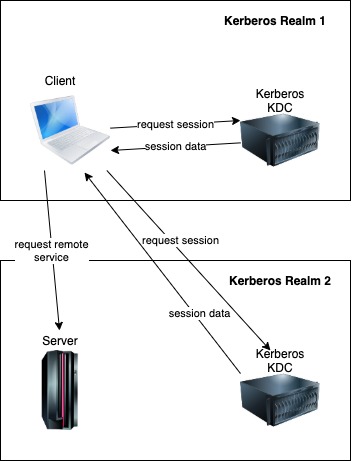
As an example, you have a user registered in your company IT system. Your company, have a contract with Microsoft and is paying them for the Office 365 subscription for all users. It would be impractical to create another user for each employee. So, in this case, you need that one Kerberos realm can authenticate users from another realm.
In this way, you can give a better service to customers/employees.
In this link, you can see how single sign-on with a KDC works and how to configure it using Kerberos.
Summary
In this post, you learned what is a KDC. The main points to remember are:
- Key hierarchy is a relevant topic to understand how a KDC works.
- The main drawback of a KDC is that it needs to be trusted.
- Using Kerberos is a way to implement a KDC in your network.
- A KDC can facilitate single sign-on to access different services in different realms. This usually translates into a better user experience to access several services in different Kerberos realms.
Related topics

