Cryptographic algorithms are susceptible to different attacks. One of such attacks is a Replay Attack.
This attack consists in the following:
- Capture the data that is transmitted.
- Re-send the data that was captured, no need to modify before resending it.
- Produce an unauthorized action.
From the description above, you can see that the attacker does not even need to modify the data.
See the steps in the picture below.
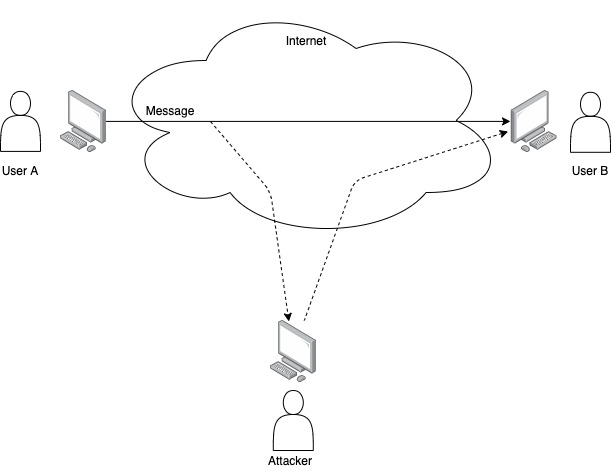
The message is usually delayed or sent several times (replay).
As an example, let’s assume two users want to establish a secure connection.
As part of the protocol, user A sends a key to user B. User C capture the key, and resend it to user B pretending that the key is coming from user A.
If user B accepts the key as user A authentication, then user C can pretend to be user A and stablish a “secure” communication with user B using the captured key.
How to prevent a Replay Attack
We can prevent this type of attack by adding a timestamp to the messages. In this case, we can prevent the Replay attack because user B can check the time stamp and realize whether it is an old message or not.
Another mechanism to avoid this type of attack is to use session keys. The session key should be random. Because of the randomness, it is not possible for the attacker to guess the next session key. You can read more about how to generate cryptographically secure random numbers/keys in this link.
A similar approach is to generate a one-time password. If the sender uses a one-time password to send the message, after a very short period of time the password will expire. So, if the receiver gets another message with the same password, it will know that the message is not valid.
Another solution is to use a Message Authentication Code (MAC). MAC is the fundamental approach to message authentication. It is a function of the message and a secrete key. It will produce a fixed-length value that we can use as an authenticator. HMAC is a combination of MAC with the result of a cryptographic hash function. It is a way to expand the use of hash functions. Read more in this link.
Related topics
