A security attack is an activity or act made upon a system with the goal to obtain unauthorized access to information or resources. It is usually carried out by evading security policies that are in place in organizations or individual devices.
Two definitions provided by RFC 4949 are:
- An intentional act by which an entity attempts to evade security services and violate the security policy of a system. That is, an actual assault on system security that derives from an intelligent threat. (See: penetration, violation, vulnerability.)
- A method or technique used in an assault (e.g. masquerade). (See: blind attack, distributed attack.)
The goal of a security attack
A security attack goal is to compromise one or more of the five major security requirements: Confidentiality, Availability, Authentication, Integrity, and Nonrepudiation.
Types of security attacks
Sometimes we overlook or not consider at all a type of security attack: physical security attack.
As its name indicates, in this case, the attacker gets access to the network or computers by being physically inside the organization.
You can understand more about how
We can classify security attacks into two groups to facilitate the study:
- Passive attacks. Does not affect the system resources.
- Active attacks. The goal is to affect system resources.
Passive attacks
The goal of this type of attack is to get access to information transmitted over the network.
Usually, the attacker will listen to the network traffic to get unauthorized access to information transmitted within the network.
An attacker listening to the network traffic can get access to private or sensitive information. After this type of attack is successful, the attacker might release private information to the public or use it for his/her own benefit.
Find below a graphical view of passive attacks.
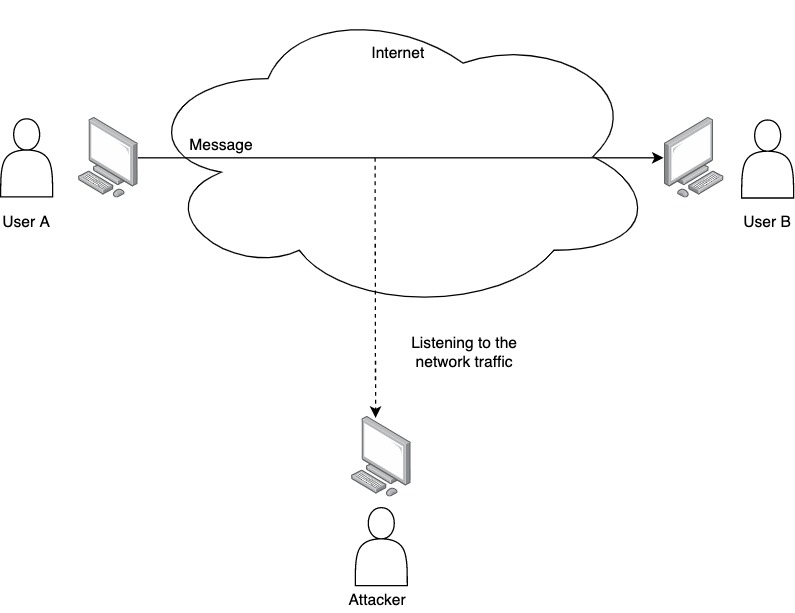
The main approach to avoid this is to encrypt the information that we send over the network. Even if the information is encrypted, the attacker can try, and sometimes be successful, to decrypt the information. That’s why it is important to understand how the cryptographic algorithms and protocols work and always to use the standards of the industry. You can get a better understanding by reading about the general concepts to study Cryptography.
Active attacks
The goal of active attacks is to alter the information. In this case, the attacker will try to modify the information that a user sent or will pretend to be someone else to gain unauthorized access to sensitive information or services.
We can divide these attacks into four categories:
- Masquerade. The attacker pretends to be someone else to gain access to information. You can read more in this post.
- Replay. This attack consists of the following: capture a data that is transmitted, re-send the data that was captured, no need to modify before resending it, produce an unauthorized action. Read more about this type of attack here.
- Modification of messages. The attacker modifies the message (part or whole) and resends it to gain access to information or resources. An active Man-in-the-Middle attack is an example in this category.
- Denial of service. This type of attack is intended to disrupt the good functioning of a network or service. For instance, the attacker can aim to stop the e-mail service of a company. If this attack succeeds, a company won’t be able to send/receive emails until the service is restored.
Find below a graphical view of active attacks.
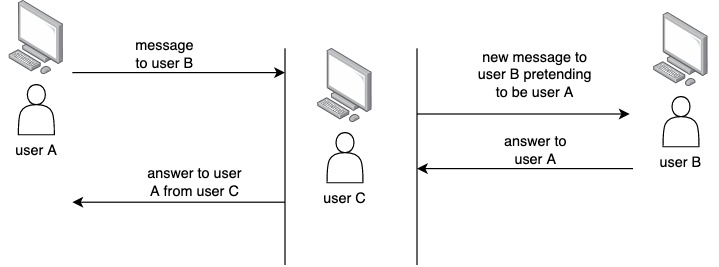
Related topics
- What is the Man-In-The-Middle attack?
- What is a Replay Attack in Cryptography?
- What is the length extension attack?
- Information security system: a resemblance with other security systems
- What is an Intrusion Detection System (IDS) and how does it work?
- What is the CIA Triad?
- What is Zero Trust Architecture?
