The CIA Triad is how computer security or cybersecurity experts refer to the concepts of Confidentiality, Integrity, and Availability altogether. These are major security goals in network security.
Let’s see the definition of each concept and some examples.
Table of Contents
Definitions
The main term related to the CIA Triad is Computer Security.
Computer Security: Measures and controls that ensure confidentiality, integrity, and availability of the information processed and stored by a computer. Source.
The term Computer Security was replaced by the term Cybersecurity. Find below the NIST definition.
Cybersecurity: Prevention of damage to, protection of, and restoration of computers, electronic communications systems, electronic communications services, wire communication, and electronic communication, including information contained therein, to ensure its availability, integrity, authentication, confidentiality, and nonrepudiation. Source.
As you can see from the definitions above, the term Computer Security and Cybersecurity are closely related to the CIA Triad. Let’s examine the definitions of each concept.
1- Confidentiality
Confidentiality refers to ensuring that only authorized individuals have access to private and/or confidential information. It is also related to individuals knowing and authorizing what information is collected from them and how is that information used.
If information is accessed by unauthorized individuals, there is a loss of confidentiality.
The link of confidentiality with cryptography is that we use encryption algorithms to ensure confidentiality. The encryption algorithms can be symmetric or asymmetric, depending on the specific situation.
2- Integrity
This concept refers to the ability to ensure that the information is modified in a pre-established way. This should provide authenticity to the information and therefore, nonrepudiation.
It also refers to systems. Unauthorized manipulation of a system, and modification or destruction of information, would be considered a loss of integrity.
To guarantee integrity we can use cryptographic hash functions, and in particular we can use HMAC.
3- Availability
The term availability is about ensuring that information and services are readily available. Also, authorized individuals should not deny access to information or services.
Availability is not provided by cryptography per se. Usually, availability is provided by network design and policies.
For instance, if we use a cloud service such as Google Cloud, Azure, etc. those services already guarantee availability because they provide redundancy. This means that service is provided using several servers (a.k.a. data centers) geographically distributed. In this case the provider ensure to provide us with availability.
Other ways to guarantee availability is to know how normal traffic looks for us, so when there is an attack to our services, we can take action. In particular, we can use Intrusion Detection Systems to ensure availability.
Common attacks to make our services unavailable are DOS and DDOS attacks.
Find below a figure that summarizes these concepts and how they are related.
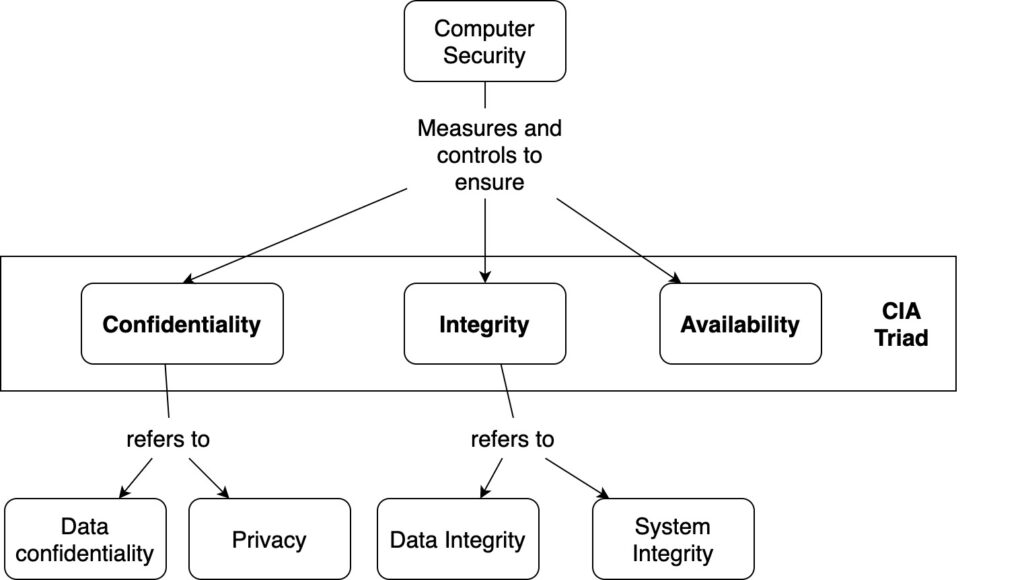
CIA Triad Examples
See below some examples of how the CIA Triad can be used to specify security risks.
Confidentiality: Bank Account details are considered confidential information. The banks are governed by several laws and your bank account details and other information that the bank possesses about you (transactions, balance, etc.) can be disclosed to certain institutions under certain conditions. These conditions and institutions vary depending on the country and the laws. In this case, your information must be kept secure by the back. If there is unauthorized access to your information in the bank where you have your account, there will be a loss of confidentiality.
Security attacks can have as a consequence loss of confidentiality. Some examples of such attacks are the Man-In-The-Middle (MITM) attack, Reply attack, and Masquerade attack.
We avoid this attacks by using the right cryptographic methods to encrypt the data. In this case, the goal is not avoid an attacker getting the data, but to avoid the attacker can understand the data. Cryptographic algorithms are known for not to be breakable in a time that matters. In other words, if they can be broken, but in many life times, we don’t need to worry about an attacker deciphering our communication with the bank to get access to our bank account.
Integrity: Following the previous example of the bank, we expect our bank account balance not to be changed by unauthorized individuals. This will be considered a huge breach of the integrity of the data related to how much money we have in that bank account.
Some attacks that can result in loss of integrity are the MITM attack and the Salami Attack.
If we create a hash of our message, and the bank establish a mechanism to verify that hash, it is easy to detect when the message comes from an unauthorized individual. In other words, the bank can identify if the message was modified or not after the autorized user send it.
It is important to notice, that we cannot use any hash function for this, it must be a cryptographic hash function. HMAC is specially used for this type of situation, as it also provides authentication.
Availability: Individuals nowadays expect to have their emails available all the time. In some cases, depending on the use of the emails, they are time-sensitive. A buy-order to a broker because of a drop in the price, a report that has to be presented on a specific day, etc. Some attackers target this type of service using the attack Denial of Service (DOS). This type of attack is intended to make, for instance, an email server unavailable to users, therefore creating situations where time-sensitive information cannot be accessed.
There are many challenges in providing effective computer security.
The requirements are simple (See the CIA Triad), but they are extremely difficult to implement. There are many things to consider like, cryptographic algorithms, implementations of those algorithms, software that enforces confidentiality and availability, and many more.
To see some of the elements involved in a security system, you can read this post I created to explain an information security system using its resemblance with another type of security system that we know better, like a physical security system in place of institutions like banks.
A way of efficiently assessing the security needs of a certain organization is defined in the OSI Security Architecture. Also, you can find here a post that explains the OSI Reference Model and the OSI Layers.
Related FAQs
What are the five major security goals in network security?
The five major security goals are considered an extension of the CIA Triad: Confidentiality, Integrity, Availability, Authentication and Non-Repudiation.
Related posts:
